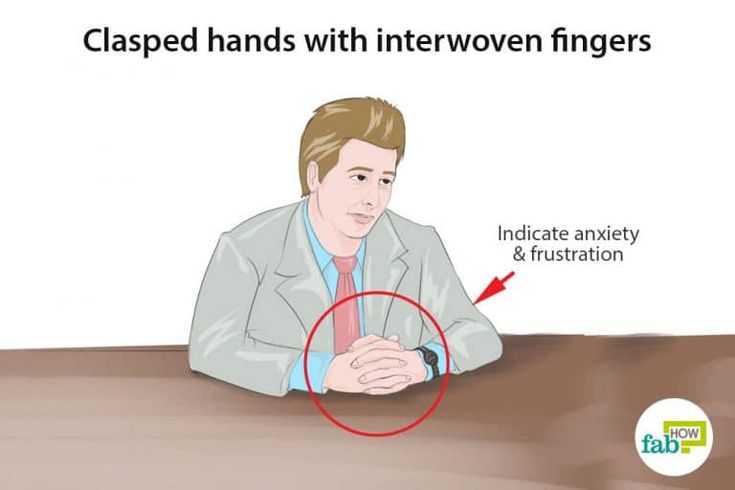
Invading my privacy
What Is Invasion of Privacy?
Invasion of privacy is the unjustifiable intrusion into the personal life of another without consent. However, invasion of privacy is not a tort on its own; rather it generally consists of four distinct causes of action. States vary on both whether they recognize these causes of action as well as what elements are necessary to prove them, so you should be sure to check your state's laws or consult with a lawyer before bringing legal action.
The four most common types of invasion of privacy torts are as follows:
- Appropriation of Name or Likeness
- Intrusion Upon Seclusion
- False Light
- Public Disclosure of Private Facts
Below, you'll find explanations and examples of each of these causes of action.
Appropriation of Name or LikenessAppropriation of name or likeness laws protect your right to control the use of your own identity for a business or economic purpose. Typically, these claims involve the unauthorized use of a person's picture or name. While state laws vary, the elements necessary to prove appropriation are generally as follows:
The defendant (the party being sued) used the plaintiff's (the party initiating the lawsuit) name, likeness or identity;
The use was for the defendant's benefit, whether the benefit is economic or otherwise;
The use was without the plaintiff's consent; and
The use caused injury to the plaintiff.
Intrusion upon seclusion laws protect your right to privacy while you are in solitude or seclusion. This right extends to you or your private affairs. For example, it's an invasion of privacy for a neighbor to peek through your windows or take pictures of you in your home. Likewise, it's also an invasion of privacy to use electronic equipment to eavesdrop on a private conversation. The general elements of this tort are as follows:
The defendant intruded into the plaintiff's private affairs, seclusion or solitude
The intrusion would be objectionable to a reasonable person
The defendant does not need to communicate the details of the intrusion to a third party; once the defendant has committed the intruding act (and the plaintiff proves the necessary elements), the defendant is liable for invasion of privacy.
False light laws protect your right to not have potentially misleading or damaging information about yourself publicly disclosed. This includes the disclosure of information that may be true but is nonetheless misleading or damaging. For example, it may be an invasion of privacy if a caption published with a photograph in a news article about a protest describes a person as a participant, when in fact, the person was only observing the protest. Generally, the elements of false light are as follows:
The defendant publicly disclosed information about the plaintiff;
The information placed the plaintiff in a false light; and
The false light would be highly offensive to a reasonable person.
Many states also require the plaintiff to prove that the defendant acted with actual malice, so be sure to check your state's laws or consult with a lawyer if you believe you may have a claim.
Public Disclosure of Private FactsPublic disclosure of private facts laws protect your right to keep the details of your private life from becoming public information. For example, publicizing facts about a person's health, sexual conduct, or financial troubles is likely an invasion of privacy. While state laws vary, the general elements of this tort are as follows:
For example, publicizing facts about a person's health, sexual conduct, or financial troubles is likely an invasion of privacy. While state laws vary, the general elements of this tort are as follows:
- The defendant publicized a matter regarding the private life of the plaintiff;
- The publicized matter would be highly offensive to a reasonable person; and
- It is not of legitimate concern to the public.
To publicize a private matter, laws generally require that private information is disseminated in such a way that it is substantially certain to become public knowledge.
Popular Example in the Media
It probably seemed like a great idea when a well-regarded suburban school district decided to loan its students laptop computers for the entire school year, even permitting the students to take the laptops home. The students, however, were unaware that the laptops were armed with internal anti-theft protection that allowed school district personnel to activate the laptops' webcams anytime without the consent or knowledge of the user. The school district used this anti-theft function to take thousands of pictures of its students studying, speaking to family members, and even sleeping.
The school district used this anti-theft function to take thousands of pictures of its students studying, speaking to family members, and even sleeping.
The so-called "Webcamgate" scandal resulted in a Pennsylvania school district paying a six-figure sum to settle the invasion of privacy lawsuit against it. While Webcamgate would have seemed far-fetched in the 1980s and 1990s, today and in the future, we can expect technology to continue to challenge our right to privacy, making understanding this right essential.
Learn More About Invasion of Privacy ClaimsIf you believe you have suffered an invasion of privacy, it's important to seek out the help of a qualified lawyer. Filing a legal claim protects your rights and can compensate you for the emotional and mental distress the invasion caused as well as for any financial or reputational harm you suffered as a result. Speak with a defamation attorney to learn more.
Not Sure If They're Invading My Privacy or Just Really Interested in Me
An analysis of 2019 ECAR student and faculty data reveals that neither faculty nor students have a strong understanding of how their institution uses their personal data; faculty have less confidence in their institutions' abilities to safeguard private data than students do.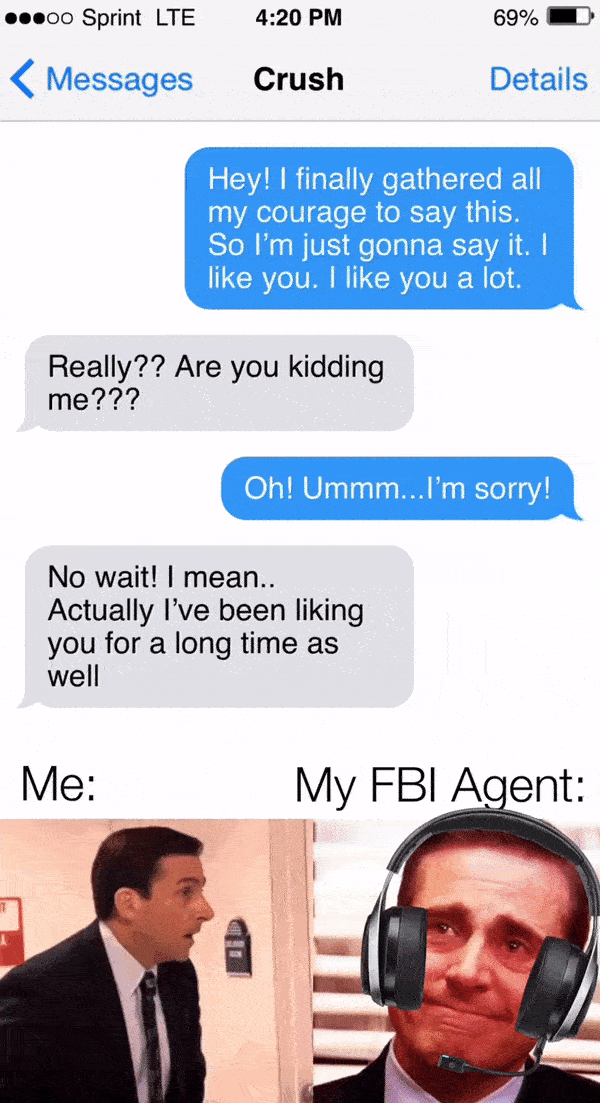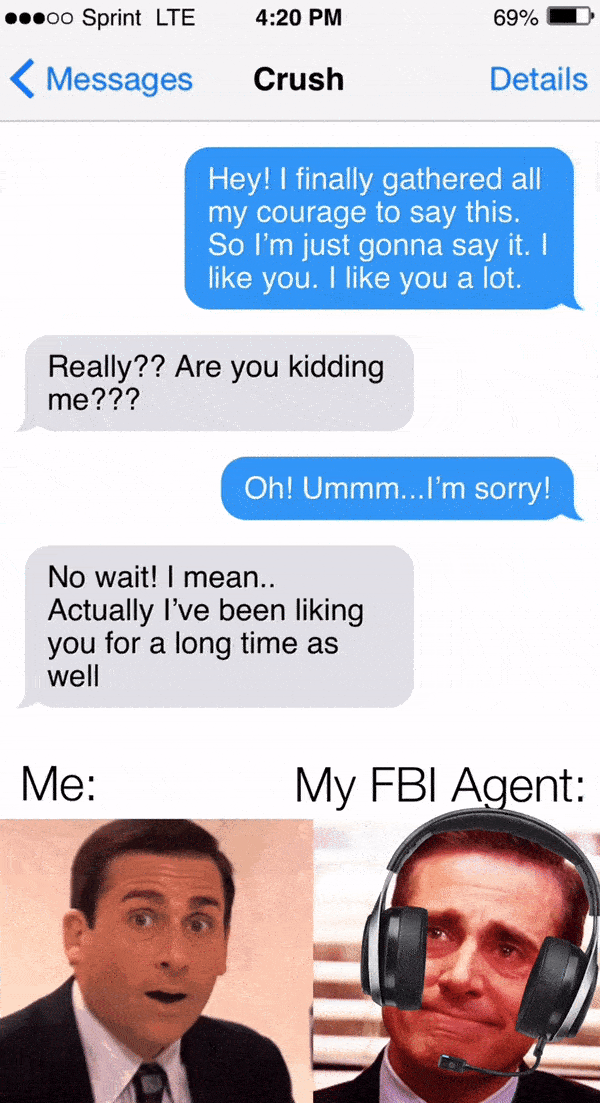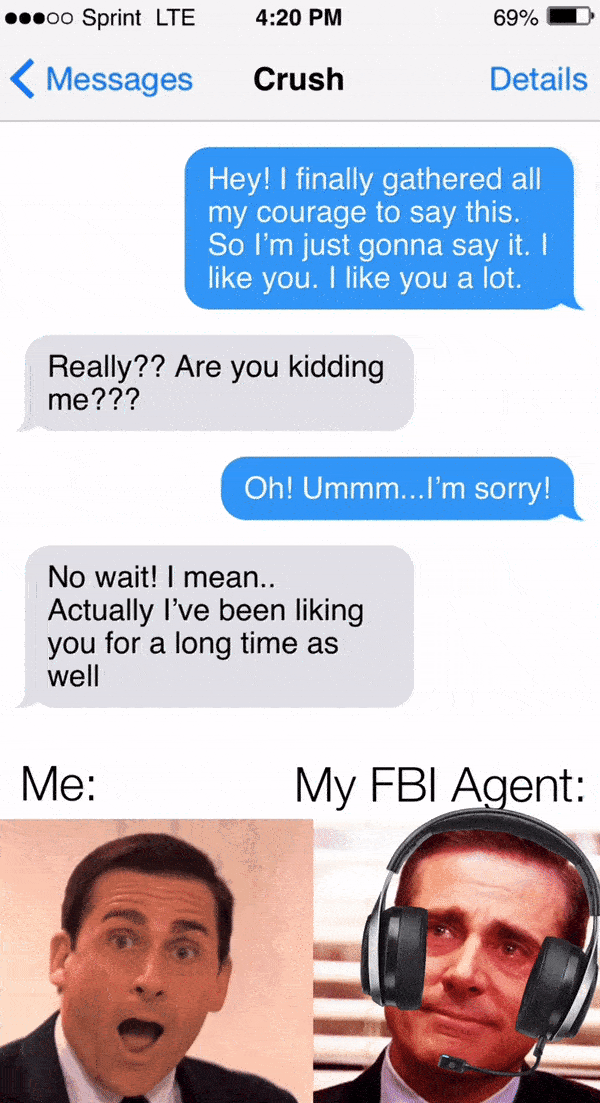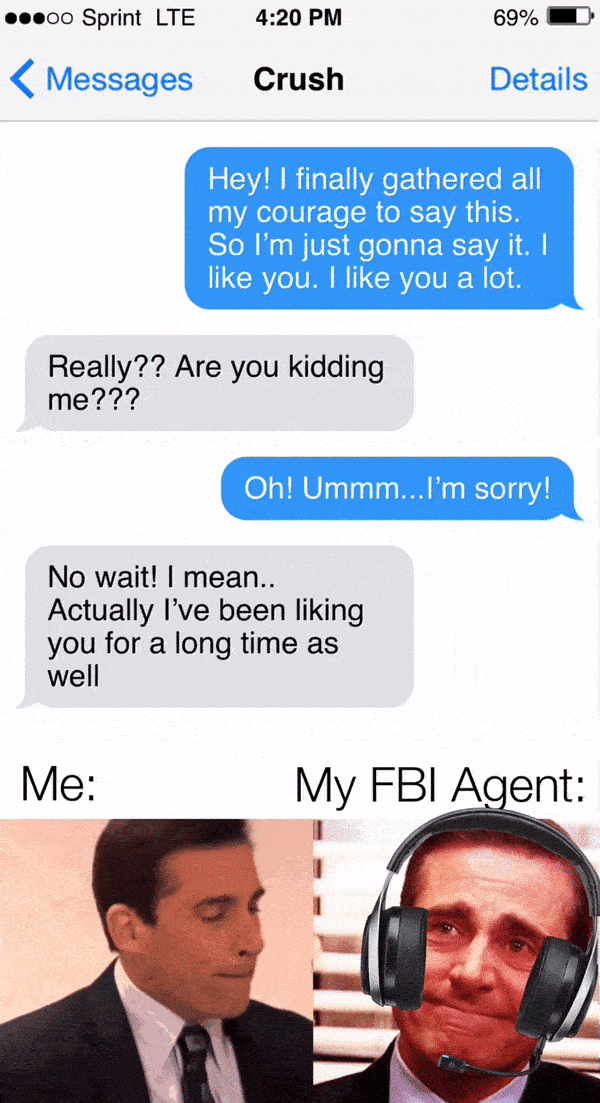
Got data privacy? Um, maybe not.
Recent news has brought attention to the widespread misuse of users' personal data on a popular social networking site.1 Given that Facebook has more than 1.59 billion daily users (that includes you, Mom and Dad!),2 we should all be concerned about data privacy. And when we wax nostalgic about the innocence of early social media networks such as Myspace (we miss you, Tom!), we are reminded that even back then, we shared a lot of personal data, someone had to curate it, and sometimes they didn't do such a great job.3
Privacy means "safeguarding institutional constituents' privacy rights and maintaining accountability for protecting all types of restricted data."4 In 2018, the FBI issued warnings to higher education institutions about attempted hacks of online payroll accounts.5 Although data breaches in education account for a smaller proportion of all reported breaches than those in sectors such as business, health care, and government, private data are clearly now a commodity. 6 Indeed, privacy came in at number three on the 2019 EDUCAUSE list of top 10 IT issues, and it's the number two issue for 2020, right behind information security strategy. Faculty and students need to be concerned about what is being collected and how it is being used.
6 Indeed, privacy came in at number three on the 2019 EDUCAUSE list of top 10 IT issues, and it's the number two issue for 2020, right behind information security strategy. Faculty and students need to be concerned about what is being collected and how it is being used.
The current generation of students, Generation Z, appears to be more concerned with data privacy and security than Millennials are.7 For example, members of Gen Z more frequently adjust privacy settings on their mobile devices and social media accounts than Millennials do.8 What are the implications of Gen Z's perspectives on information security and data privacy at a time when institutions are seeking to leverage data analytics to improve student success?9 Meanwhile, faculty data are used for employment, human resources (HR) records, and institutional analytics. What are their perspectives on the collection and use of private data?
We surveyed these two important groups of institutional IT end users—faculty and students—and examined their knowledge and understanding of institutional policies and practices surrounding the use of their personal data, as well as their confidence in the ability of their institution to safeguard personal data. Students reported a reasonably high level of confidence in their institution's ability to protect their data. However, we found that faculty and students alike generally have low understanding of how their personal data are used at their institution.
Students reported a reasonably high level of confidence in their institution's ability to protect their data. However, we found that faculty and students alike generally have low understanding of how their personal data are used at their institution.
A majority of faculty (60%) understand relevant policies surrounding data use, storage, and protection (see figure 1). When faculty start to contemplate what's going on with their personal data, their understanding gets murkier. Less than half (44%) understood what personal data their institution collected on them, and even fewer (24%) understood how their institution used their personal data.
Figure 1. Faculty understanding of institutional data policies, collection, and useGiven that faculty are somewhat puzzled about what personal data are being collected and how those data are being used, it is perhaps not surprising that their confidence in whether personal data are being safeguarded is shaky. Since 2017, faculty confidence in their institution's ability to safeguard their own personal data, student data, and research data has declined. There was a 21 percentage-point decrease in confidence in institutional information security practices and a 17 percentage-point decrease in confidence in their institution's ability to safeguard research data (see figure 2).
There was a 21 percentage-point decrease in confidence in institutional information security practices and a 17 percentage-point decrease in confidence in their institution's ability to safeguard research data (see figure 2).
These declines are disconcerting since faculty attendance at institutional security training increased between 2017 and 2019, suggesting that training alone is not enough to instill confidence or understanding. That said, if faculty are attending more training than in previous years, they might have greater awareness of data security issues and therefore might be more skeptical about personal data security in light of society's increasing concerns regarding personal data.
A strong majority of students (70%) were confident in their institution's ability to safeguard their data (see figure 3). However, when looking at knowledge of institutional use of personal data, less than half of students (45%) thought they benefit from the collection of their personal data for purposes such as improved services and advising; similarly, just 44% said they understand how their institution uses personal data. This lack of knowledge might be particularly relevant for institutions that use advising technologies or analytics for student success. Gen Z views data sharing as transactional, and they expect something of value in return.10 Although students have confidence in their institutions, this is only part of the security equation for Gen Z. It might be in institutions' best interests to communicate what is being collected and how it can benefit students, particularly if schools want to leverage student data to improve student outcomes and services.
11
However, when looking at knowledge of institutional use of personal data, less than half of students (45%) thought they benefit from the collection of their personal data for purposes such as improved services and advising; similarly, just 44% said they understand how their institution uses personal data. This lack of knowledge might be particularly relevant for institutions that use advising technologies or analytics for student success. Gen Z views data sharing as transactional, and they expect something of value in return.10 Although students have confidence in their institutions, this is only part of the security equation for Gen Z. It might be in institutions' best interests to communicate what is being collected and how it can benefit students, particularly if schools want to leverage student data to improve student outcomes and services.
11
Institutional leaders should emphasize that cybersecurity practices are more than a list of rules to be followed and should explain how these practices benefit the entire campus community. 12 Emphasizing the importance of student data privacy, several states have passed privacy laws that protect students' personal data. Between 2013 and 2018, a total of 35 state laws were passed that prohibit institutions of higher education from selling student data or that protect privacy and property rights to electronic communications.13 As organizations of all kinds collect ever larger amounts of personal data about users, and as data breaches (inadvertent and malicious) continue to threaten the exposure of those data, these laws will likely become more ubiquitous; as more legislation is enacted, institutions ideally will communicate to students and faculty how these laws protect privacy. Moreover, institutional data security might become as much of a selling point for students as is a seamless Wi-Fi network. As a new generation of faculty is hired, they will likely share students' views on personal data. Higher education should plan accordingly to address privacy concerns.
12 Emphasizing the importance of student data privacy, several states have passed privacy laws that protect students' personal data. Between 2013 and 2018, a total of 35 state laws were passed that prohibit institutions of higher education from selling student data or that protect privacy and property rights to electronic communications.13 As organizations of all kinds collect ever larger amounts of personal data about users, and as data breaches (inadvertent and malicious) continue to threaten the exposure of those data, these laws will likely become more ubiquitous; as more legislation is enacted, institutions ideally will communicate to students and faculty how these laws protect privacy. Moreover, institutional data security might become as much of a selling point for students as is a seamless Wi-Fi network. As a new generation of faculty is hired, they will likely share students' views on personal data. Higher education should plan accordingly to address privacy concerns.
IT departments need to facilitate a culture of security by ensuring understanding and confidence in their institutions' security practices.14 Faculty confidence is concerningly low. And both faculty and students lack a comprehensive understanding of how their data are being used and protected. Talking to the campus community about compliance sends the message that following policies is important. Communicating to faculty and students that their data are being safeguarded can contribute to a culture of cybersecurity on campus. Ensuring that faculty and students understand what personal data are collected, how they are collected, and how they are safeguarded can reinforce the importance of institutional cybersecurity. Got data privacy? Institutions need to let you know if you do.15
Editor's note: The original version of this blog post contained errors in the data and figures and in the interpretation of the data. The current version corrects those errors, and the text has been revised to reflect those corrections.
For more information and analysis about higher education IT research and data, please visit the EDUCAUSE Review Data Bytes blog as well as the EDUCAUSE Center for Analysis and Research. For more on information security governance, compliance, data protection, and privacy programs, please visit the EDUCAUSE Review Security Matters blog as well as the Cybersecurity Program page. Access additional information security and data privacy resources through the Awareness Campaign page.
Notes
- Davey Winder, "Facebook Privacy Update: Mark Zuckerburg's Response to Cambridge Analytica Scandal One Year On," Forbes, March 19, 2019. ↩
- Facebook, Company Info, accessed September 19, 2019. ↩
- Niraj Chokshi, "Myspace, Once the King of Social Networks, Lost Years of Data from Its Heyday," New York Times, March 3, 2019; Tom Anderson was the founding president of Myspace. ↩
- Susan Grajek and the 2018–2019 EDUCAUSE IT Issues Panel, "Top 10 IT Issues, 2019: The Student Genome Project," EDUCAUSE Review, January 28, 2019.
 ↩
↩ - Federal Bureau of Investigation Public Service Announcement, "Cybercriminals Utilize Social Engineering Techniques To Obtain Employee Credentials To Conduct Payroll Diversion," accessed September 19, 2019. ↩
- "Data Breach QuickView Report," Risk Based Security, Inc., November 2019. ↩
- Seventy-seven percent of students surveyed for ECAR Study of Undergraduate Students and Information Technology, 2019 are members of Generation Z, defined as those who are 22 or younger at the time of the survey. See Michael Dimock, "Defining Generations: Where Millennials End and Generation Z Begins," Pew Research Center, January 17, 2019, for information on defining Generation Z; Gina Pingitore, Vikram Rao, Kristen Cavallaro, and Kruttika Dwivedi, "To Share or Note to Share: What Consumers Really Think about Sharing Personal Information," Deloitte Insights, September 5, 2017. ↩
- Ibid. ↩
- Amelia Parnell, Darlena Jones, Alexis Wesaw, and D.
 Christopher Brooks, "Institutions' Use of Data and Analytics for Student Success," Results from a National Landscape Analysis (2018). ↩
Christopher Brooks, "Institutions' Use of Data and Analytics for Student Success," Results from a National Landscape Analysis (2018). ↩ - See, for example, Goldie Blumenstyk, "Big Data Is Getting Bigger. So Are the Privacy and Ethical Questions," The Chronicle of Higher Education, July 31, 2018; From Innovation to Expectation — How M&E Leaders Are Responding to Gen Z, research report (Los Angeles, CA: EY Global Media & Entertainment, n.d.). ↩
- Martin Kurzweil and Mitchell Stevens, "Setting the Table: Responsible Use of Student Data in Higher Education," EDUCAUSE Review 53, no. 3 (May/June 2018). ↩
- Thomas Skill, "The Coming Generation Z Impact on Cybersecurity," Education Technology Insights, n.d. ↩
- Amelia Vance, "Privacy Laws Protecting Student Data," Security Matters (blog), EDUCAUSE Review, January 29, 2018. ↩
- See the Social Proof section of Jessica Barker, "The Human Nature of Cybersecurity," EDUCAUSE Review, May 20.
 2019. ↩
2019. ↩ - Nathan Fisk, "Toward an Academic Culture of Security," Security Matters (blog), EDUCAUSE Review, October 10, 2016. ↩
Joseph Galanek is a Senior Researcher at EDUCAUSE.
Ben Shulman is a Statistician at EDUCAUSE.
© 2019 Joseph D. Galanek and Ben Shulman. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
- ParentTopics:
-
Data Privacy Faculty Development Privacy Student Technology Use
Please enable JavaScript to view the comments powered by Disqus.
- via Twitter
- via Facebook
- via LinkedIn
- via email
Advertisement
Advertisement
Advertisement
The Supreme Court of Russia clarified what constitutes an interference with privacy /TASS/. Intervention in personal life becomes a crime when it comes to information that the citizen himself did not want to make public.
 This was explained by the plenum of the Supreme Court of the Russian Federation in the resolution adopted on Tuesday "On some issues of judicial practice in cases of crimes against the constitutional rights and freedoms of man and citizen (Articles 137, 138, 138.1, 139, 144.1, 145, 145.1 of the Criminal Code of the Russian Federation)".
This was explained by the plenum of the Supreme Court of the Russian Federation in the resolution adopted on Tuesday "On some issues of judicial practice in cases of crimes against the constitutional rights and freedoms of man and citizen (Articles 137, 138, 138.1, 139, 144.1, 145, 145.1 of the Criminal Code of the Russian Federation)". "When deciding on the presence in the actions of a person of the corpus delicti provided for by part 1 or 2 of article 137 of the Criminal Code of the Russian Federation (“Violation of privacy”), the court must establish whether his intent covered
At the same time, the collection or dissemination of such information in state, public or other public interests cannot entail criminal liability, "as well as in cases where information about private the life of a citizen has previously been made public or has been made public by the citizen himself or by his will."
The collection of information about the private life of a person, explained the Supreme Court, "is understood as deliberate actions consisting in obtaining this information in any way, for example, by personal observation, listening, questioning other persons, including recording audio, video, photographic means, copying documented information, as well as by stealing or otherwise acquiring them.
Dissemination of information about a person's private life consists in communicating (disclosing) it to one or several persons orally, in writing or in any other form and in any way, including via the Internet.
In addition, criminal liability for violation of the secrecy of correspondence or telephone conversations (Article 138 of the Criminal Code of the Russian Federation) occurs regardless of the presence in them of information constituting a personal or family secret.
"Under article 138 of the Criminal Code of the Russian Federation, illegal actions that violate the secrecy of correspondence, telephone conversations, postal, telegraphic or other messages of specific persons or an indefinite circle of persons are subject to qualification, if they are committed with direct intent. In this case, liability under this article occurs regardless of whether whether the information transmitted in correspondence, negotiations, messages constitutes a personal or family secret of a citizen or not," the plenum explained.
"Other messages" provided for in Article 138 of the Criminal Code of the Russian Federation are sms and mms messages, facsimile messages, instant messages transmitted via the Internet, e-mails, video calls, as well as messages sent in another way. "When considering criminal cases on a crime under this article, the courts should keep in mind that the secrecy of correspondence, telephone conversations, postal, telegraphic or other messages is recognized as violated when access to correspondence, negotiations, messages is made without the consent of the person whose secret they are constitute, in the absence of legal grounds for restricting the constitutional right of citizens to the secrecy of correspondence, telephone conversations, postal, telegraphic and other communications," the resolution says.
Illegal access to information about incoming and outgoing connection signals between subscribers or subscriber devices of communication users (date, time, duration of connections, subscriber numbers, other data allowing to identify subscribers) is also a violation of the secrecy of telephone conversations, the plenum emphasized.
Illegal access to the content of correspondence, conversations, messages may consist in familiarization with the text and (or) materials of correspondence, messages, listening to telephone conversations, audio messages, copying them, recording them using various technical devices, etc.
According to judicial statistics, last year 63 people were convicted under this article in Russia, in 2016 - 50 people.
Tags:
Russia
Invasion of privacy. Crime and Punishment
Sergei Petukhov, RIA Novosti columnist.
On October 1, the law on the protection of the private life of a citizen, adopted by the State Duma on June 21 and signed by the president on July 2 this year, came into force.
July 3, 2013, 13:57
The law on the private life of citizens was adopted in RussiaThis law for the first time introduces a rule on the protection of citizens in cases of dissemination of false, but not discrediting information about them, for example, information about a non-existent victory of a citizen in a competition.
Even at the stage of discussing the law, there was a lot of controversy about whether it would take the "servants of the people" out of public control. Many then even believed that the law was initiated by officials and deputies, frightened by the publications on the Internet of information about their business, unseemly connections, foreign assets, and about their children and household members who successfully use these assets.
And so this law came into force. Probably, it's time to take a closer look at who he can really complicate life for.
What the law protects and from what
The law protects us from the so-called "intangible goods" that belong to each of us from birth (or guaranteed by law): our life, health, personal integrity, honor and good name, business reputation, inviolability privacy, personal and family secrets, the right to free movement, the choice of place of stay and residence, the right to a name and the right of authorship.
If encroachments on all these intangible benefits of a citizen are quite material, rude and weighty, such as, for example, a slap in the face or illegal expulsion from the house where we live, then the Criminal Code protects us from this.
In this case, we are talking about non-material attacks on private life, that is, the collection, storage and dissemination of information about the private life of a citizen. The law introduces responsibility for this, because these actions can, under certain circumstances, destroy a family, a good name, and finally lead to a heart attack. Even if a citizen only feels such a threat, now he has the right to apply to the court to stop it.
Why was such a law needed
Indeed, why? After all, the Criminal Code has a law on libel, and the Civil Code has always had articles protecting honor, dignity, privacy and other intangible benefits. There were even as many as three articles there - from the 151st to the 152nd "note". Why was it necessary to amend them and add another 152nd article under number 2?
Why was it necessary to amend them and add another 152nd article under number 2?
The fact is that since 1994, when the current Civil Code was adopted, our life has changed, a new reality has appeared in it in the form of the Internet, and a hole has appeared in the code.
He protected from encroachments on the intangible benefits of a citizen in the media or in documents emanating from organizations, but in principle he could not protect against the same on the Internet. A blog is not a media outlet, and even official documents about a citizen posted on a blog are not a document coming from a legal entity.
Bloggers used their freedom from legislation actively and not always for the benefit of the citizens they discussed, inflicting quite material and sometimes very significant damage on them. And since some of these citizens had the right to initiate legislation, they initiated and adopted a law that eliminates this gap in the legislation.
What's new is prohibited
It prohibits everything that was prohibited by the Civil Code in its previous version, only now these prohibitions also apply to the Internet. Now any citizen, having felt a threat to his intangible benefits due to the dissemination of private information about him on the Internet, has the right to call the offender to court. And if the court recognizes the guilt of the latter, he will answer to the fullest extent of the Civil Code, first of all by deleting his post.
Now any citizen, having felt a threat to his intangible benefits due to the dissemination of private information about him on the Internet, has the right to call the offender to court. And if the court recognizes the guilt of the latter, he will answer to the fullest extent of the Civil Code, first of all by deleting his post.
Some opponents of the law still cherish the hope that this will not affect retweets and reposts of illegal information, they say, nothing is said about its duplicates in the law. Vain hopes. It is said very clearly and unambiguously: "A citizen has the right to demand the deletion of the relevant information, as well as the refutation of the specified information in a way that ensures that the refutation is brought to the attention of Internet users."
How can the refutation be communicated to network users? By the same route that the original information spread. There is simply no other way on the Internet.
When public and public interests help
After patching up the gap for bloggers in the Civil Code, the deputies did not stop and introduced the whole article 152 (2) "Protection of a citizen's private life", which was not previously in the Civil Code.
The inability to stop in time often harms people's choices. Although it would probably be wrong to blame them for this. If we recall our national history, then this seems to be our common national trait.
The new article does not fundamentally introduce anything new into Russian legislation. It only in a concentrated form focuses on the fact that it is prohibited "without the consent of a citizen, the collection, storage, distribution and use of any information about his private life, in particular information about his origin, about his place of stay or residence, about personal and family life ".
But having said "a", the legislators were forced to say "b" as well, because a full stop after this passage would have paralyzed the work of all domestic media. Officials with deputies would lose channels for disseminating information about their work, not to mention PR.
It is impossible to ask the consent of an official or a deputy every time: “Can I write that you graduated from college before you got this job? Would you mind if we write that you come from a simple working-class family and have achieved everything since childhood with your work and talent? Will you not sue if it becomes known that you are now in Kemerovo at a meeting with your voters?" And so on.
Therefore, the second paragraph of the law appeared, which says that "the collection, storage, distribution and use of information about the private life of a citizen in state, public or other public interests is not a violation of the rules established by the first paragraph of this paragraph."
The practice of law enforcement is well known to all of us. But in this case, these same "public or other public interests" will greatly interfere with its usual course. An experienced lawyer can learn a lot from them.
For whom the law on the protection of privacy is dangerous
A blogger who purposefully rots an official or deputy has at least some justification left: they say that he acts in the interests of society. And an ordinary network "hamster" who does not climb into high politics, but collects, stores and distributes information about the private life of, for example, his boss, or a neighbor, or a colleague he likes - how will he justify himself now?
Now the post about the fact that the ex-wife, whom she took out of Moldova, where she grew up in a family of alcoholics, did not see that she had three children from her two previous husbands, whom she left in the maternity hospital, gave her everything, and she , such and such, with the director Yakin, now drove off to Sochi for the Olympics, becomes sued immediately for six indicators.