How to cyberstalk
How to Cyberstalk Someone Without Being a Terrifying Creep
By
Lindy West
Comments (136)We may earn a commission from links on this page.
Probably the best thing about the internet is that it allows you to KNOW EVERYTHING IMMEDIATELY. Is a moose bigger than a horse? What's a "Kylie Jenner"? Does zucchini bread count as a vegetable? Could I beat a deer in a fight? What the fuck is the Huffington Post? It's a beautiful thing, this internet, though not without its pitfalls. Nowhere are the internet's beauty and its pitfalls so apparent as in the realm of romance.
For the first time in human history, huge swaths of the dating pool have voluntarily cataloged their own intimate details and drunken photos for the ready, instant browsing of any creepy goober with internet access. Your crushes, your exes, your potential OKCupid dates—pretty much all of them are going to have some sort of online presence, if you know where to look (which, come on, you obviously do).
This can be great, if you want to vet tomorrow night's date for pick-up artist tendencies, Republicanism, or wintertime flip-flops. Or, it can be terrible, if you get so caught up in the virtual life of the guy you lost your virginity to that you knit a set of dog-socks when his beagle gets sick and mail them to him even though you two haven't spoken since 1998. That is BAD. DO NOT DO THAT. For all its boons, the internet is basically an automated crossing-the-line machine.
Arwa Mahdawi at the Guardian has an excellent roundup of guidelines for how to investigate a potential mate without getting caught and spending the rest of your life in shame-prison (or, worst case scenario, actual prison). My personal favorites:
Don't compile a dating dossier
There's a point at which a little light stalking goes from "research" into "psychopathic behaviour". The point at which this line is crossed is up for debate. Nevertheless if manila folders are ever involved you can be pretty certain you're in weirdo territory.
My friend Britta, for example, went back to the apartment of a guy she'd been dating for a couple of weeks to discover he had a folder labelled "Britta" in plain view on his desk. "I was sitting on his lap at the time so I asked him about it," said Britta. "And he pulled out a bunch of random photos from my Facebook page. It was awkward for both of us."
Do destroy the evidence
While you may not have a binder full of women on your desk, a little online research can leave a very large trace. Getting out your phone to show your date a hilarious YouTube video of prancing pygmy goats (everyone does this, right?) only to realise that their LinkedIn profile is still open on your screen is a serious first-world problem. My normal advice in situations like this would be to drink copiously. However, I'm a little worried that someone I'm semi-interested in would think less of me for suggesting this. So, in case she's stalking my digital footprint, let's, errr, move swiftly on.
In short, cookies are never your friend, and clear your history if you want any chance of a future.
Do know how much stalking is too much stalking
Seven pages into Google is too much.
Seconded, all of it. But this is a juicy topic, and I think we can come up with plenty more (leave yours in the comments!). Here are a few that came to mind for me:
1. DON'T DO CRIME.
When I say "cyberstalking," I do not actually mean stalking someone on the cyberweb. I'm just calling it that as kind of a winky, self-deprecating exaggeration—like, you know, oh, haha. DO NOT ACTUALLY STALK ANYONE EVER. The point of creepin' on crushes and exes on the internet is to torture yourself, not your target. Once simple online curiosity crosses the line into real-world contact and obsession, shit isn't cute anymore. If you have trouble telling the difference, here's a helpful exercise. Ask yourself: "If Gary Busey was doing to me what I'm doing to Chad right now, would I call the cops?" If the answer is anything above a "Yeah, maybe," go jump into a very cold body of water.
2. Be careful with your fingers.
For the love of all that is sacred, do not accidentally click "like" on some random pic from 2009 that you found during a 3 am spelunking expedition into your hot barista's old Facebook albums. NEVER EVER CLICK "LIKE" ON ANYTHING INVOLVING A BIKINI OR NAKED MUSCLES. Just to be safe, never click on anything at all.
3. Don't tell yourself scary stories for no reason.
Oh, are there six new photos of your crush playing Big Buck Hunter with some harlot who's totally pulling off that haircut you've always been afraid to try because of the time your mom told you your neck was "hefty"? You could stay up all night crying and writing elaborate, obsessive erotic fan-fic about the two of them and their "Big Horn Sheep Adventure," OR you could just tell yourself she's probably his sister or something and then get back to binge-watching Alias on the 'Flix. If those are your choices, why the fuck would you pick the first one? Pick better. Be better at picking.
Be better at picking.
4. When in doubt, Spicoli that shit.
In moments of romantic uncertainty and pain and diminishing rationality, I always think of something my older sister once told me. You just gotta be Spicoli. Would Spicoli cry in the coffee shop over some shit on Instagram? Definitely nope. Would Spicoli eat a whole tube of cookie dough because the hot guy from French ignored his friend request? Nah. Would Spicoli let a few measly photos of his ex-girlfriend visiting a corn maze with the entire lacrosse team distract him from enjoying chimichanga night? HELL NO. Spicoli would just be chill, man. Whatever. He's Spicoli. If you ever feel your romantic obsession levels reaching such a pitch that they're distracting you from living your life, channel Spicoli. Carry around a laminated picture of Spicoli in your wallet, like a totem, if you must. Be the Spicoli you wish to see in the world.
Image via Valeriy Lebedev/Shutterstock.
Cyberstalking: strategies | Take Back The Tech
Every situation is different, but it's never your fault. You may feel helpless, but you can take action. Here are some tested strategies for people experiencing cyberstalking or worried that it might happen.
Mobile Phones
Protect your data
Take care with intimate photos. Phones are easily lost and stolen, which makes their data vulnerable. Transfer sensitive photos to a more secure location, such as a USB stick, as soon as you can. While they are on your phone, encrypt them and keep them in a password-protected file.
-
Turn off automatic cloud saving. Every photo you take on your iPhone is automatically uploaded to Apple’s iCloud. To turn off iCloud sharing, go into Settings > iCloud > scroll down to Photos and slide the option to off To disable iCloud completely, go to the bottom of the menu and hit “delete account.” On Android phones, photos can be backed up to the Google+ cloud service, but this will be off when you first set up a Google account.
 Double check your settings going to the Photos app > select General Settings > slide Auto-Backup to Off. Check your cloud frequently to know exactly what is stored there.
Double check your settings going to the Photos app > select General Settings > slide Auto-Backup to Off. Check your cloud frequently to know exactly what is stored there. -
Erase data before recycling. If you plan to pass your phone on, first make sure none of your info is on it. Remove the SIM card. Return the phone to its factory settings. For Android, go to settings > privacy > select Factory Data Reset. Instructions vary with different models, so consult the manual or the internet.
Guard your privacy
-
Password-protect your phone. This will keep your data safer if you lose your phone or someone tries to use it without your permission.
-
Be aware of itemised telephone bills. Some telephone bills itemise numbers dialed and messages sent.
-
Consider an alternate SIM card for private calls. Turn your phone off, switch out SIM cards and restart your phone.
 Don't forget to remove the private card when you're finished and keep it in a safe place.
Don't forget to remove the private card when you're finished and keep it in a safe place. -
Know the trade-off between security and convenience. When you install apps, they may be convenient, but they can make you (or your friends) vulnerable. Think of all the times installing an app using your Facebook password requires you to give away your list of contacts to the app maker. Do you know how they use that info?
Hide your location
-
Only enable GPS settings when you need them. The majority of smartphones have GPS chips that can geo-locate the phone in seconds. Do you need this on all the time? You usually activate GPS in Settings > Privacy > Location.
-
Disable the GPS on your mobile camera. This geographic info can be embedded in photos pinpointing exactly when and where the photo was taken. Together with the content, it can be easy to discern where you live, work or play.
 Check your manual for instructions. For example, on an iPhone, go to Settings > Privacy > Location, and disable the option of ‘Camera’.
Check your manual for instructions. For example, on an iPhone, go to Settings > Privacy > Location, and disable the option of ‘Camera’.
Social media
Yoel Ben-Avraham
Think about what you share online. It is very easy to glean information about where you live, the places you love to go to in your area and the people you care about from posts and pictures. Treat your email and/or internet account like you would your credit card, ID or passport numbers – very carefully.
Account registration
-
Create a different email account for site registration. This will help avoid spam, and your personal email won't be revealed if the online service doesn’t have good privacy practices.
-
Leave optional fields blank. When registering online, only fill in the required fields and leave certain identifying information such as birthdate blank.
-
Use a profile photo that doesn’t identify you.
 Choosing images that also protect your location can keep you from being recognised or found.
Choosing images that also protect your location can keep you from being recognised or found. -
Choose a screen name that isn't personal. Many people have screen names that do not give away identifying characteristics. You might want to consider a user name that is gender-neutral.
-
Check your privacy settings. Services such as Facebook change their privacy policy all the time, so check in regularly to make sure you are sharing the information you want to share only with people you trust. Some sites have options for you to test how your profile is being viewed by others. You can find social networking privacy settings here.
-
Use sites with good privacy policies . Make sure that your the providers and platforms you use have acceptable privacy policies that prohibit cyberstalking or online harassment. If they have none, suggest they create them and/or switch to a provider that is more responsive to user privacy concerns.
 See how Take Back the Tech! has evaluated Facebook, YouTube and Twitter.
See how Take Back the Tech! has evaluated Facebook, YouTube and Twitter.
Online practices
-
Never post your personal contact details publicly. And don't share anyone else's. People often post their phone numbers in Facebook comments without considering that everyone else can see it. Use direct messaging instead.
-
Search yourself. Do a regular internet search on your name to monitor where you appear online or set up an alert.
-
Choose a screen name that isn't personal. Many people have screen names that do not give away identifying characteristics. You might want to consider a user name that is gender-neutral.
-
Reset passwords regularly. Yes, it's a pain, but critical. Security-in-a-box has a good chapter on strong passwords and tricks for remembering them.
-
Keep your technology updated and secure.
 Read our tips for tools and install (and update!) the relevant software. Choose open source when you can.
Read our tips for tools and install (and update!) the relevant software. Choose open source when you can. -
Know the trade-off between security and convenience. Do you really need to install that new app if you aren't 100% sure it won't make your device vulnerable?
Blogs & websites
-
Use an alternative address to register domain names. When you register a domain name, your contact information is made public and available for anyone to see. This is a transparency requirement in many countries. While domain proxy services exist for a fee to protect privacy, these have proven unreliable in the face of legal or public pressure to reveal registry information. You might use an organisational address and phone number or one that does not reveal your home location. Create an email account exclusively for managing the domain.
-
Don’t post your email address. Instead, create a simple contact form where users can submit their information in order to contact you.
-
Require accounts in order to post comments. You can also activate the option to track IP addresses of commenters.
Denouncing stalkers and seeking redress
-
Move fast to block the stalker. Lots of people don't take action because they think they are overreacting, but repeat attacks may paralyse you. Record incidents (time, place, event). If you take action quickly and block the stalker's opportunities to harass you, they may lose interest.
-
Make it clear that you do not want to be contacted. Warn that any further contact will result in a police report. Communication may stop right there. Write once and document it.
-
Save copies of all communication. Even though the immediate desire might be to delete the communication and try to forget about it, record-keeping is crucial. Take screenshots and back up evidence on a USB stick or external hard drive.
 You'll need electronic copies, as the coding that accompanies all cyber communications is the only way to verify authenticity.
You'll need electronic copies, as the coding that accompanies all cyber communications is the only way to verify authenticity. -
Report, block or filter emails. You can filter a particular email address so that it goes directly to “junk” or to a folder that you specify. That means you don't need to read the emails, but they are still available as evidence. Learn how to turn on filtering and blocking capabilities. Gmail has a reporting mechanism if a stalker is using their email service.
-
Block blog and chat room trolls. You can block unwanted chat room contacts by checking the chat room instructions. If you own a blog or website and someone posts harassing comments continuously, you can block them using an ‘IP address block’. Blog providers like WordPress offer installable widgets. Or check with your website provider.
-
Unpublish abusive posts, but don't delete them. These are part of the evidence that you will want to provide to the police or the internet provider.
 If you are receiving harassing phone calls, record them for evidence.
If you are receiving harassing phone calls, record them for evidence. -
Contact the stalker's ISP. Contact the harasser's internet service provider. Most ISPs prohibit using their service for abusive purposes. An ISP can often intervene by directly contacting the stalker or closing the account. Document this contact.
-
Ask a friend to moderate abusive comments. Save your energy for what is important and have trusted friends moderate the crap.
-
Go to the authorities. More women being harassed online are choosing to go to the authorities, which has led to changes in legislation. If the harassment involves hate groups, threats of death or bodily harm and/or public postings of your location or contact information, you should contact law enforcement right away. The more evidence you have collected, the faster they can act.
-
Get emotional support. Tell your family and friends you are being stalked.
 Their support is critical during the stalking and in the aftermath to help you cope.
Their support is critical during the stalking and in the aftermath to help you cope. -
Inform your employer if necessary. If you think this person may harass you in the workplace, it's important to notify your employer. Your boss will be more likely to back you up if they later receive communication from the stalker, and they may be able to mitigate professional damage and providing evidence.
-
Clean up the damage. If your internet searches reveal that the stalker published information about you, Take a look at “How to delete things from the internet” for more information. Key steps:
-
Request that websites take down of the information
-
Contact Google to remove information
-
Rebuild a positive online reputation to “bury” the negative search results
-
Report legal violations to search engines
-
Make a legal case for defamation
-
Issue:
Cyberstalking
Internet Safety for Children: Cyberbullying and Cyberbullying
Lesson 3: Cyberbullying and Cyberbullying
/en/tr_ru-internet-safety-for-kids/-predators/content/
stalking
Cyberbullying
Cyberbullying is bullying that occurs online, often through instant messaging, text messaging, emails and social media. Cyber bullies may be the same age as their victims, or they may be older. If the bully is an adult, they are usually referred to as a cyberstalker or cybercriminal. nine0005
Cyber bullies may be the same age as their victims, or they may be older. If the bully is an adult, they are usually referred to as a cyberstalker or cybercriminal. nine0005
Cyberbullying can be just as painful as other types of bullying, and in some cases even worse. Cyberbullying is not limited to the playground; this can happen any time children use the Internet, even if they are at home. In addition, the bully may sometimes remain anonymous, making the bullying difficult to stop.
Examples of cyberbullying
Cyberbullying can take many forms. The following are some examples of what could be considered intimidation:
- Writing mean things through instant messaging, texting or online gaming
- Posting demeaning messages on social networking sites
- Posting or sharing obscene photos or videos
- Creating a fake profile to humiliate someone
The following resources provide useful information about cyberbullying, including helpful actions for children and teens:
- Stopcyberbullying.
 org: Created by WiredSafety.org, this site contains information for children ages 7 to 17.
org: Created by WiredSafety.org, this site contains information for children ages 7 to 17. - Cyberbully411.org: This site contains information resources for children and teens, including communication strategies for parents about cyberbullying.
- Common Sense Media: The site offers detailed guidance on working with children ages 2 to 17.
- KidsHealth: This site has an article that gives a detailed understanding of cyberbullying. nine0020
WiredSafety.org contains general information about Internet safety. For more information on cyberbullying, watch the video provided.
Response to cyberbullying
It is very important to teach your children how to respond to cyberbullying. To do this, you can invite your children to follow these guidelines when they are being bullied.
Bully blocking in Microsoft Messenger
- Don't answer the bully. Often bullies want a reaction from their victims. If you ignore them, then they may lose interest.
- If possible, block messages from the bully. If the bullying occurs in a chat, email, or social networking site, there is usually an option to block all messages from the bully.
- Keep all e-mails and other messages sent by the bully. You may need to use them as evidence at some point. nine0020
- Report the bullying to a parent or trusted adult. If the bullying continues, tell your parents or an adult you can trust (such as a teacher) to help you deal with the problem.
Is your child a cyberbully?
Cyberbullying
Sometimes kids can be mean. Unfortunately, the Internet often makes it easier for people to say nasty things because it is more impersonal and anonymous than real life. As a result, many children engage in cyberbullying even though they do not consider themselves to be bullies at all. nine0005
nine0005
It is important for your children to understand that comments made on the Internet can hurt just as much as a face-to-face comment. Make sure they know not to say things online that they wouldn't say in person.
In addition, children can face serious consequences for cyberbullying. Many schools have a zero-tolerance policy for bullying, which can include cyberbullying that occurs outside of school. In some cases, students have even been suspended from school for cyberbullying. nine0005
For more information, read the article "Could Your Child Be a Cyber Bully?".
Resources
The following resources provide useful information about cyberbullying, including activities for children and teens:
- Stopcyberbullying.org: This site, created by WiredSafety.org, contains information for children ages 7 to 17.
- Cyberbullying - How to Calm Down a Bully Part 1 & Part 2: Created by middle and high school students, this video series is based on the spy movie theme to show how to deal with cyberbullying.
 nine0020
nine0020 - Cyberbully411.org: This site contains resources for children and teens, including strategies for communicating with parents about cyberbullying.
- Common Sense Media: This site offers detailed guidance for working with children ages 2 to 17.
- KidsHealth: This site has an article that gives a detailed understanding of cyberbullying.
Previous: Stay Safe From Online Intruders (Predators)
Next:Safe use of social networks (Social Networks)
/en/tr_ru-internet-safety-for-kids/-social-networks/content/
Yoair Blog is a global anthropology blog post.
Message Views: 19,979
Cyber stalking is one of the most dangerous crimes of the 21st century. And it took the lives of many people all over the world, young and old. But mostly teenagers.
Even without regard to ethnicity, the number of cases of cyberstalking has increased over the years. nine0005
An estimated 6-7.5 million people are stalked in the US in one year. Nearly 1 in 6 women and 1 in 1 men have experienced persecution at some point in their lives. Extracted from Fact of Persecution.
For some people like me who have been victims of cyber stalking, we know it can be a nightmare. Hence, in this article, we will look at cyberstalking and its impact on victims.
Before we dive in, let's first define cyberstalking. nine0005
What is cyber stalking?
Image Credit: MediumDefined by Wikipedia, Cyberstalking is the use of the Internet or other electronic means to harass or harass any person, group, or organization. It may include false accusations, slander, slander, and slander. This may also include monitoring, identity theft, threats, vandalism, solicitation for sex, doxxing, or blackmail.
Internet stalking, electronic stalking and online stalking are all terms used to describe cyber stalking. nine0005
nine0005
The term “cyber stalking” became known around the 1990s. But the concept of using the internet (and/or social media) for stalking purposes has been around for a long time since the inception of the internet.
Cyber stalking is an extreme form of bullying that can range from sexual harassment to death threats.
In a recent survey, 60% of adults said they had experienced cyberbullying, and 78% of those people said it had a detrimental effect on their lives. nine0005
Cyberstalker
Image Credit: Protect NowCyberstalker is a term used to describe a person who uses social media to harass, threaten or intimidate another person, often to extort money or get information from them. Cyberstalkers can be ex-partners, envious people, or even strangers who seek to create trouble.
Examples of cyberstalking
- Using fake social media profiles to track the activities of their victims
- Imagine yourself as a friend or loved one of the victim to befriend the victim and get information about him.

- Using victims' personal information without their consent to damage their reputation or contact another person
- Post offensive comments on message boards or chat rooms
- Distribution of sexual photographs of the victim or their loved ones, fake or real.
- Installing a GPS gadget on the victim's car so that he can track his every move. nine0020
- Use of emails to threaten the victim, friends and relatives.
- Hacking and saving emails, text conversations and social media messages
Is there a difference between cyberbullying and cyberstalking?
Image Credit: NordVNPCyberstalking and cyberbullying are two terms that are often used interchangeably. Although they may appear to be similar offences, they are slightly different.
Cyberbullying
Cyberbullying is a form of bullying that uses electronic devices such as cell phones, computers or tablets to transmit harmful content. This is also known as digital bullying.
Cyberbullying is difficult to define because it can be as simple as playing a joke on a person and spreading it to others. Or it could be extreme, like posting a nude photo of a person without their permission.
Cyberbullying can be as simple as sending an email to someone asking you not to contact them, but it can also include threats, sexual remarks, and derogatory labels. nine0005
A common misconception is that cyberbullying only affects teenagers, but the reality is that cyberbullying can affect anyone.
Cyberbullying can happen to anyone and is not limited to any age group, gender, sexual orientation, race or religion.
However, cyberbullying affects teenagers and children. is mostly while cyberbullying affects adults. Teenagers or children experience cyberbullying through social networking sites such as Facebook, Twitter, Instagram and Snapchat. nine0005
cyber stalking
Cyber stalking is when someone uses electronic means of communication in such a way that "you feel fear. " This is not just a harmless joke. It can do real harm to your mental health.
" This is not just a harmless joke. It can do real harm to your mental health.
Moreover, cyberstalking is a form of bullying that involves the use of technology to harass a person, often by sending unsolicited e-mails, instant messages, or Internet postings. Cyber stalking may also involve the use of technology to track someone's whereabouts or to harass and threaten a person. nine0005
However, cyber stalking is a rapidly growing problem. The hardest part about these cases of cyberstalking is identifying them. It is not easy to distinguish between a person who is too friendly and a person who is crossing the line. And many people are unlikely to realize that they are targets until a cyberstalker attacks them.
What are the results of cyberstalking?
Cyber stalking can have extreme psychological and emotional consequences for the victim, and in some cases stalking can escalate into physical stalking or violence. nine0005
In addition, cyber stalking has many dangerous consequences, but the most obvious one is that it can damage your mental health. Cyber stalking can make you feel anxious, neurotic, depressed, and post-traumatic stress disorder. This can cause a lot of suicidal thoughts.
Cyber stalking can make you feel anxious, neurotic, depressed, and post-traumatic stress disorder. This can cause a lot of suicidal thoughts.
In the United States of America, cyberbullying has caused several homicides in the past ten days. Cyber stalking is a real issue that is much more common than people think and is something we all need to be aware of. nine0005
Moreover, cyber stalking is the third most common motive for murder in the US. In the UK, this is the second most common motif.
A recent study found that cyberstalking is associated with a 27% increase in suicides. A study published in the Journal of Adolescent Health found that more than two million people aged 10 to 29 are victims of cyberbullying each year.
Women experiencing cyberbullying
Image Credit: Cyber Bullying Org Cyberbullying is a problem that women often suffer from. According to the Bureau of Justice Statistics, women are more likely to be victims of cyberbullying than men. Since the majority of victims of cyberbullying are women, the perpetrators are more likely to be men.
Since the majority of victims of cyberbullying are women, the perpetrators are more likely to be men.
A recent study found that four out of five women have experienced cyberbullying and two out of three women have experienced cyberbullying. The problem is so widespread that almost half of women under 30 have decided to give up social media altogether. nine0005
Why are women more likely to be cyberstalked than men?
Amanda Hess's post Why Women Are Not Welcome on the Internet stirred up many people's feelings.
But aren't women welcome on the Internet for sure?
Image Credit: MalwarebytesCommunity Contribution to Cyber Harassment of Women
Women are more likely to be victims of cyber harassment than men because there is a power imbalance between men and women in society. Women are more likely to be harassed by a stranger because they are considered weaker and more vulnerable people. nine0005
Social media activity of women and men
Studies show that women are often victims of cyber harassment because they are usually more active on social media than men. Of the 74% of social media users, 76% are women and 72% are men.
Of the 74% of social media users, 76% are women and 72% are men.
It is very important to remember that cyberbullying can happen to anyone. While women are more likely to experience this than men, cyberbullying is not limited to one gender. Basically, be aware of the warning signs and take steps to protect yourself. nine0005
What did the government do?
Image Credit: Lawrence Ryan investigationCyber stalking laws vary by state, but the most common stalking and harassment charges are five years in prison and a fine.
Legislation
Since 1999, various regulations have been in place to combat cybercrime, such as cyberstalking.
In India, for example, Section 500 of the Indian Penal Code deals with defamation. And it can be used if the stalker uses the victim's personal information to publish an offensive message or comment on any electronic medium. Any such act is punishable by up to two years in prison, a fine, or both. nine0005
The US has a law against cyber stalking. Harassment is illegal under U.S. Code Section 2261A, which has been updated to include penalties for anyone who "uses mail, any interactive computer service, electronic communications service, or electronic communications system" to harm, threaten, harass, assault, or spy after another person.
Harassment is illegal under U.S. Code Section 2261A, which has been updated to include penalties for anyone who "uses mail, any interactive computer service, electronic communications service, or electronic communications system" to harm, threaten, harass, assault, or spy after another person.
And in South Africa, on December 116, 1998, Law No. 15 on Domestic Violence came into force 1999 (Act), which provides much-needed effective and affordable legal procedures for victims of domestic violence. And in South Africa, Domestic Violence Act 116 of 1998, Section 1 of the Act defines "domestic communication" and protects South Africans from cyberbullying and harassment.
However, some countries do not have cyber stalking laws.
Directors of Information Security
Governments have appointed a Director of Information Security (CISO). Their responsibility is to identify and document the security requirements that arise from every technical innovation. Their role is to recommend the security measures needed to protect members of the public from cyber harassment.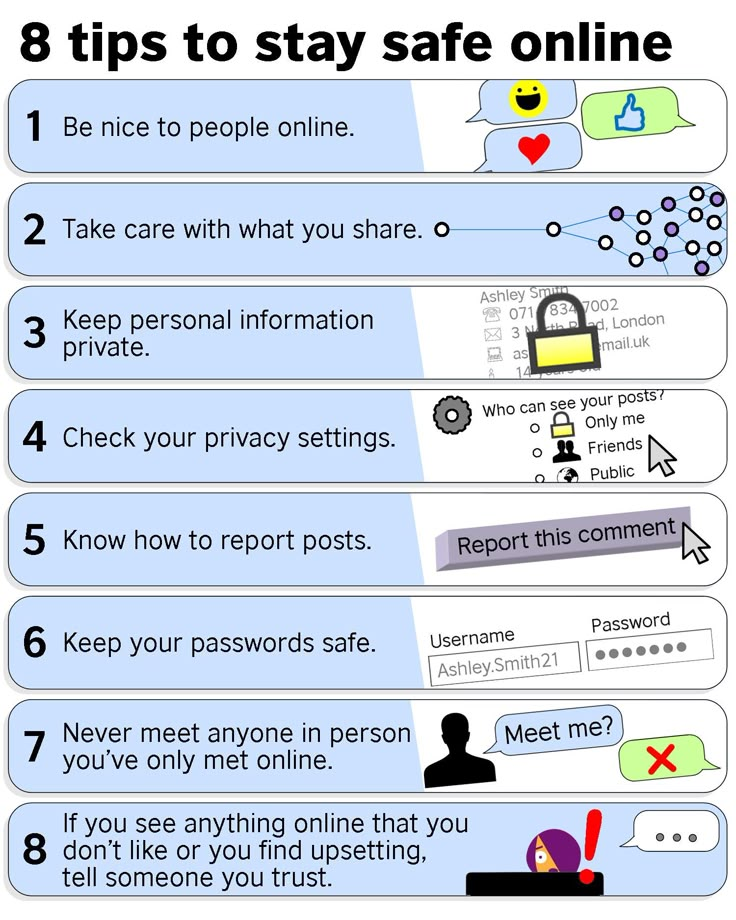 nine0005
nine0005
How to protect yourself from cyber harassment
Image Credit: Indian Institute of Legal StudiesWebsite Audit
To make sure that your site is not hacked, you should check it regularly. Hackers will try to infect your site with malware or set up links to other sites that may contain dangerous software.
When you audit your website, you look for security holes, weaknesses in your design, and places that can be used to attack your business. You're also looking for red flags that indicate you don't take cybersecurity seriously. nine0005
Credit card check
Check your credit history annually to make sure there are no unauthorized accounts or credit cards associated with your identity. The easiest way to do this is to get a credit report from each of the three credit agencies (Experian, Equifax and TransUnion).
Avoid sharing your personal information
To begin with, don't post too much personal information on social media and be careful what you share. Secondly, if you're going to post something possibly private, make sure you use the privacy settings on your social network. nine0005
Secondly, if you're going to post something possibly private, make sure you use the privacy settings on your social network. nine0005
passwords
The first thing you can do to keep yourself safe is to change your passwords regularly. You should change your passwords at least once a month, making them long and complex. The longer the password, the harder it is to guess. And the more complex the password, the harder it is to crack.
Don't accept friend requests from strangers
Protect your social media accounts by only accepting friend requests from friends. Go to your privacy settings and change the settings so that only friends can see your photos and messages. If you want to allow friends of friends to view your posts, make sure you set the minimum number of friends in your settings. nine0005
Social networks and their response to cyber harassment
Image Credit: Tiger Mobiles Facebook has 1.55 billion active users at the latest. And Twitter has 313 million active users. There are many people and many opportunities for cyberstalkers. But fortunately, social media also has measures to combat cyber harassment.
There are many people and many opportunities for cyberstalkers. But fortunately, social media also has measures to combat cyber harassment.
Social networks such as Facebook have measures in place to combat cyber harassment. Facebook has privacy settings that allow you to keep your profile private or public, as you see fit. You can choose who can see your profile, photos, messages, etc.
Social networking site Twitter is now taking action to combat online cyber harassment. Twitter can block accounts you don't want to see. You can also disable keywords, which will help you block tweets from accounts you don't want to see.
You can now report abuse in tweets. And Twitter will review them within 24 hours. Twitter also makes it easier to report abusive accounts and close accounts that break the rules. nine0005
Instagram has a great set of tools to help you manage cyberstalkers on your account and let them know you're not interested in continuing the conversation. You can block them and report them on Instagram and they will take it from there. You can also report people who bully you or send you inappropriate messages.
You can block them and report them on Instagram and they will take it from there. You can also report people who bully you or send you inappropriate messages.
There are a few things you can do to prevent cyber stalking on Instagram. Block the person first and then inform them on Instagram and demand that your account be removed from their follower list. You can also protect yourself from being hacked using two-factor authentication. nine0005
With all these measures to combat and reduce cyber stalking, why is the number of cyber stalkers increasing?
Image Credit: Panda SecurityLawmakers say cyberstalking is on the rise as social media use rises. As social networking sites continue to expand and grow, there will be even more opportunities for cyberstalking.
Due to the anonymity of the Internet, allegations of stalking are generally difficult to prosecute. When someone cyber-stalks a victim online, they are often able to hide their identity, making it difficult for law enforcement to track them down. While this makes it difficult to prosecute cyberstalking cases, it does not preclude them. nine0005
While this makes it difficult to prosecute cyberstalking cases, it does not preclude them. nine0005
Cases of cyberbullying are on the rise because many victims do not disclose information about cyberbullying to the authorities. Society often ignores cyber harassment. Many victims are confused by their cyberstalking situations and do not want to report their condition.
Misunderstanding. Even if they are victims, some people do not know how to recognize cyberstalking crimes. Some people don't know that cyberstalking is a crime.
In consolidation
We have an obligation to protect ourselves and limit our online activities. Unfortunately, there is no way for us not to become victims of cyber harassment; instead, we are provided with knowledge on how to avoid becoming victims of cyberstalking.
Even if you are a victim, contact the police or law enforcement immediately. Messages should not be forwarded or deleted. Save them for later use as evidence.
Our lives matter.