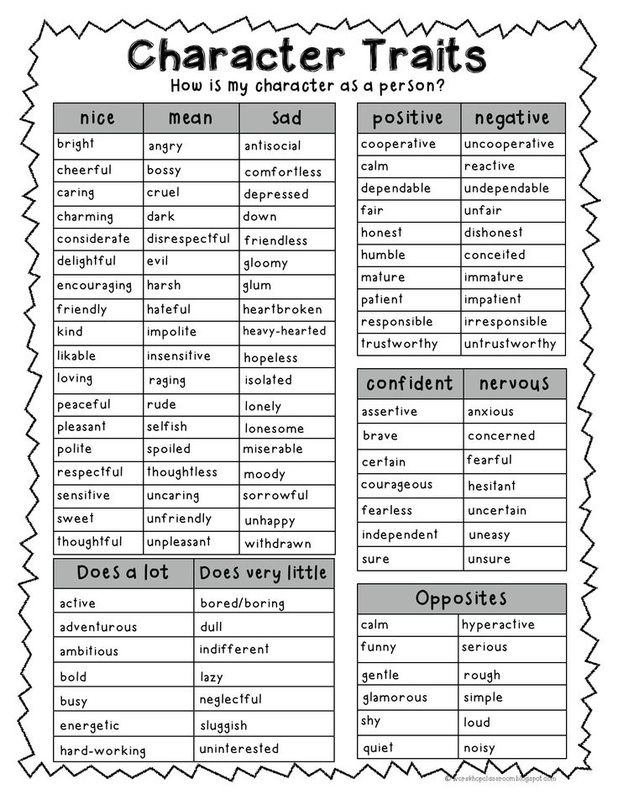
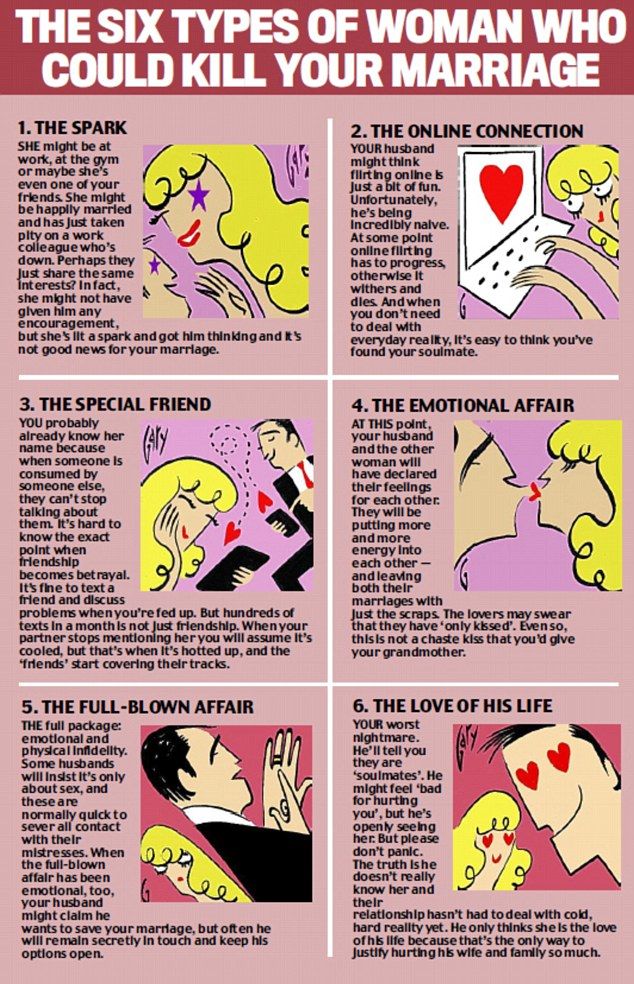
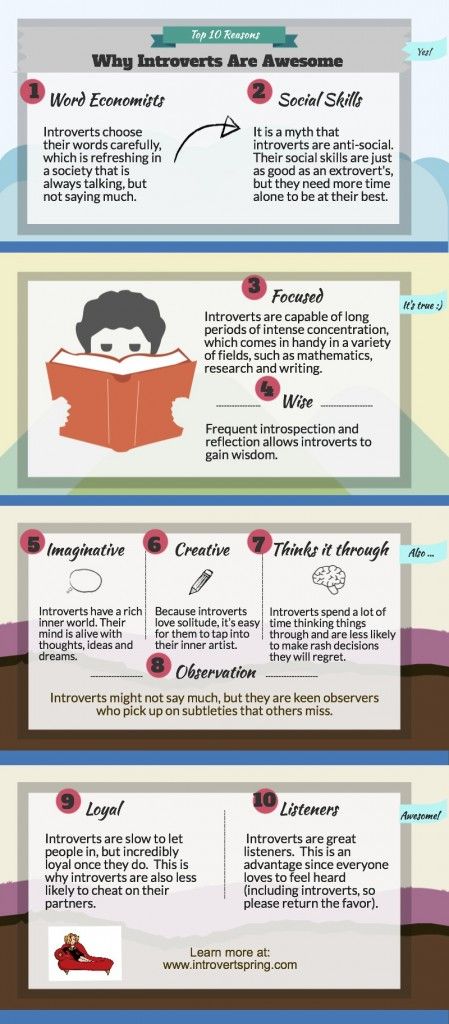
Characteristics of a cheating man
15 Characteristics of a Cheating Man You Need to Know
“Love is blind” might be the most truthful statement ever made when it comes to spotting a habitual cheater.
Too often, women see their husbands as heroes and not ordinary men with cracks in their armor.
A cheater’s behavior patterns tell us more by watching than by asking.
According to a 2018 study by the General Social Survey, up to 20% of men have cheated on their wives.
Men 35 and older are more likely to admit they have cheated, with 65 and older being the highest group of tell-tale cheaters.
What Is One Thing All Cheaters Have in Common?
Several characteristics of a cheater stand out, so nailing down just one isn’t easy.
Even one overarching theme among habitual cheaters splinters into different categories.
A cheater’s behavior patterns are mostly centered around a need being unmet.
It could be sexual exploration, trying something new, or getting the admiration that comes in the early stages of any relationship.
Ladies, sit down.
This doesn’t mean you ARE NOT meeting your man’s needs. You have done nothing wrong.
Sometimes men don’t even know they have that need until they find it in someone else.
Men need to find their words to tell you when they aren’t happy, and you need to understand a cheater’s behavior patterns and serial cheaters’ personality traits.
15 Characteristics of a Cheating Man You Need to Know
Several of a cheater’s behavior patterns might be actions that initially attracted you to them. Love is blind, but it’s also deaf and mute sometimes.
We see things as we want to see them, and now, these tips can help you see things as they really are.
1. He Lacks Impulse Control
This guy says, “Just one more drink” four times before you leave the barbecue.
He goes to the hardware store to get paint and comes home with a new lawn mower. He splurges on a new suit while you’re saving for a family vacation.
Men who lack impulse control could find themselves in a regretful situation on the next business trip to Las Vegas. Temptation is the same no matter what person, place, or thing is available.
Temptation is the same no matter what person, place, or thing is available.
2. He’s a Flirt
His flirting was adorable when you first met. The way he pursued you, smiled with those dimples, or gently touched his hand on your lower back as you were talking.
It stops being adorable when you are two kids into a 10-year marriage, and he’s doing any of that with a colleague at a work party.
Set boundaries early in a relationship regarding inappropriate behavior and what you believe to be cheating. If flirting is off the table, stand firm. Cheating doesn’t always have to mean sex outside the marriage.
3. He’s an Opportunist
Fatal Attraction was the epitome of a man taking advantage of an opportunity. In the end, it didn’t work out so well for the mistress or the bunny.
If your man is always seizing an opportunity, it could indicate future behavior. A cheater’s behavior pattern that is opportunistic generally means there was no intent to cheat – he just couldn’t help himself.
Notice how your husband acts when he does seize a regular opportunity – maybe it’s taking the front row parking spot when he knew another car was going to park there. Does he feel guilty? Victorious? The response says a lot.
4. He Compartmentalizes
Imagine if that one thing that really bothers you, like guilt feelings, could be stored in a box, closed, locked, and put away until the next family dinner. You can’t see, think, or ruminate over it. That’s the skill of compartmentalizing.
Men are particularly good at compartmentalizing thoughts and feelings, so the two never cross paths. If your man can compartmentalize well, that means he potentially could easily box, close, and lock any indication of an affair while around you.
5. He is Narcissistic or Has Narcissistic Traits
The word “narcissist” is thrown around on social media, describing any selfish person or deed.
However, narcissists go far beyond selfishness. They lack any ability to feel guilt or remorse. They are always wearing a mask of who they THINK they should be in society’s eyes.
They are always wearing a mask of who they THINK they should be in society’s eyes.
To better understand, think of the last time you ate a banana. You were hungry for that banana. You peeled it, ate the whole thing, and threw away the peel. Then you went on with your day. You never thought twice about that banana peel sitting in the trash.
To a narcissist, you are that banana peel. You serve a purpose and then get discarded without a second thought. Rinse, repeat.
6. He Gaslights You
“You’re crazy!” is the anthem of gaslighters. He manipulates conversations to make you appear forgetful, confused, or outright crazy.
It can be as simple as pretending you never told him about dinner with the neighbors, even though you told him, texted him, and put it in his calendar. He will still insist you never clearly communicated it to him.
The problem with gaslighting is that many women want to fix the situation or move on from it and say, “Okay, fine. I don’t want to argue about it.”
I don’t want to argue about it.”
This just adds more gas to the proverbial lamp for next time until he comes home late four nights in a row without an explanation and sings the “You’re crazy!” song before going off to bed.
7. He Has Personal Experience with Cheating
Men who witness parental infidelity could be destined for the same fate. Either a man sees his dad, “the hero,” do it, so it MUST be okay, or he could see his mother cheat and become terrified his own wife will cheat.
That anxiety bubbles up, and some will choose to “cheat first” in a relationship. On the other hand, he could also say, “Well, my parents worked through it, so we can too.”
More Related Articles
35 Disturbing Signs of Gaslighting In A Relationship
11 Best Ways to Stop Loving Someone Who Doesn’t Love You Back
Did One Of You Cheat In Your Marriage? 10+ Common Reconciliation Mistakes To Avoid
8.
 He Cheated With You
He Cheated With YouThis habitual cheater has a love story with you that usually starts along the lines of, “You can’t help who you fall in love with, right?” The fact that a cheater is with you, even if you didn’t know he was a cheater at the beginning, means they are familiar with the behavior.
Women also lose some ground when complaining about a potential habitual cheater because “What did you think was going to happen considering how you two met?”
You don’t “deserve” to be cheated on. Period.
9. He Has Low Self-Esteem
A cheater’s behavior pattern could be as simple as not feeling good about themselves and looking for any chance to get an ego or endorphin boost.
A study published in Psychology Today reveals that 57% of men blame their own low self-esteem as the main driver behind cheating. He might think you nag on him too much, which beats him down.
He could also feel so bad about himself that he ignores his need to self-improve but instead seeks that validation outside the marriage.
10. He’s Suddenly Ravenous in Bed
Intimacy can tone down after the honeymoon until it becomes a scheduled or seldom act. Some couples even have to plan sex to adapt to busy lifestyles.
If you suddenly find your man trying new tricks or buying you lingerie, he might be cheating with someone else and trying out his new moves on the woman he married.
11. He’s Accusing You of Cheating
Famous trial lawyer Louis Nizer famously said, “When a man points a finger at someone else, he should remember that three of his fingers are pointing at himself.”
Whether the accusation stems from guilt, is a defensive tactic, or is an act of gaslighting, there’s truth to that statement. Especially if your schedule and daily patterns haven’t changed in the slightest, yet he’s still accusing you, start snooping.
12. He Has a Great Poker Face
You’ve watched several times as your husband convinced his mother Sunday night is booked with a business dinner, and you’ve celebrated the win when he gets away with it.
That same ability to tell someone he loved a bald-faced lie indicates a remarkable ability to hide the truth from people he loves.
Be extra worried if he also has #6 and #4 down pat.
13. He Guards His Mobile Devices Like They Contained Nuclear Codes
Trust and respect for privacy go a long way in a healthy relationship, but there should be no reason your husband would hide things from you, change a passcode on the phone often, or walk out of the room when the phone rings.
If your husband won’t let you see his phone, call list, photos, or app downloads, there is definitely something going on with his boundaries in the relationship. It might be cheating, or it might be another thing he’s hiding.
14. He’s Super Tech-Savvy
Our apologies to all the good men out there who happen to have taught an iPhone to whistle Dixie.
However, a man with expert knowledge of apps, downloads, organization, and social systems is likely to find all the ways to hide things on a device and all the apps that he can use for untraceable contact.
Be especially suspicious of his activity if he uses the Kik app.
15. He Has ADHD
“SQUIRREL!” Dug said in the hit Disney Movie Up when he was mid-sentence and got distracted. Men with ADHD can have their own “SQUIRREL” moments, otherwise known as “Shiny New Things.”
A 2019 book, ADHD After Dark, highlights the main challenges when one person in a relationship has ADHD and the other doesn’t.
One top finding of this study was that men with ADHD are more likely to be cheaters because they focus on the new, exciting relationship and become hyper-focused on it, even to the detriment of their family.
Final Thoughts
Do you hear that noise? That’s your brain overanalyzing every move your man has made in contrast to every point listed above.
There is a lot to be said about the gut feeling that your man is cheating on you, but it’s a far cry from proof.
Do not confront your husband until you don’t even have to ask, “Are you cheating on me?” because you already have all the proof you need.
Men Who Cheat – What Makes Husbands Cheat
Media Platforms Design Team
Certainsigns of infidelity
are clear: lipstick on the collar, smell of perfume and Sunday-night business meetings. But there are less-obvious characteristics that almost all cheaters share. Do one or two of these a philanderer make? Not necessarily. But if the below rings true about your guy and your instincts tell you something's not right, you might want to check that collar.
1. He's secretive, especially about his phone. He's on it more often (and often outside), he ignores calls, he changes his passcode frequently or he suddenly starts leaving it in the office or car. He's trying to lock you out of his life, literally and figuratively. "Trust your gut here and confront him," says Danine Manette, a professional investigator and author of
Ultimate Betrayal: Recognizing, Uncovering and Dealing with Infidelity. "Most betrayed women report that they saw this sign, but either ignored it or explained it away."
"Most betrayed women report that they saw this sign, but either ignored it or explained it away."
2. He's no mama's boy. "Watch out for a man who's angry at his mom," warns Carole Lieberman, MD, author of Bad Boys: Why We Love Them, How to Live with Them and When to Leave Them. If he lies or speaks unkindly to her, they have a dysfunctional relationship, explains Dr. Lieberman. Men who disrespect their moms tend to disrespect their wives too. Assume that he's able to lie to you just as easily.
3. He's insecure. Whether about his appearance (he's losing his hair) or his job (he was just fired), feeling threatened can be a trigger to boost self-esteem with an affair. That's because cheating can make him feel like a man again, says Dr. Lieberman. If you've got a guy who's down on himself, don't flaunt your own desirability to other men or boast about your accomplishments at work. Instead, encourage him to reach for his goals.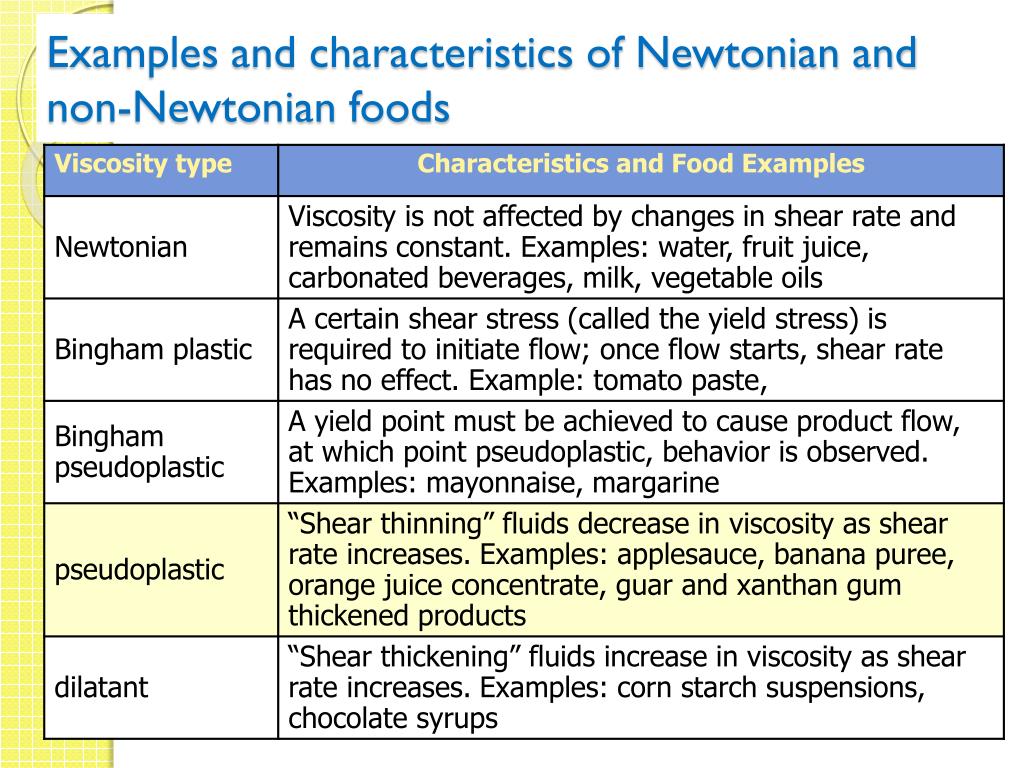
4. He's forgetful. Was he never particularly absentminded before? Cheaters commonly pretend to forget things they're actually pretty sure of, says Deborrah Cooper, a San Francisco dating advisor for Examiner.com and author of the forthcoming When to Break Up: The Fast & Easy How to Guide for Getting Out of Relationships That Suck. Rather than mix up your details with hers, he may find it safer to "forget" your favorite restaurant or even your birthday. If he asks lots of questions he should know the answer to—like wanting to know which movie you're seeing when you've told him twice—reply with a question of your own. "Labor Day—remember, you said you'd let me have my chick flick this time?" If his response is akin to a student stammering when called on unexpectedly in class, keep your eyes peeled for other clues.
5. He's a narcissist. Men who are immature and self-centered, like a spoiled child, are primed for serial cheating, insists Ramani Durvasula, PhD, a clinical psychologist and psychology professor at California State University, Los Angeles. "Narcissists lack empathy and view women as objects. Plus, they believe they have a right to do whatever they want," says Dr. Durvasula. She maintains the best thing to do is get out. "You can't change him, and he doesn't want to be changed."
"Narcissists lack empathy and view women as objects. Plus, they believe they have a right to do whatever they want," says Dr. Durvasula. She maintains the best thing to do is get out. "You can't change him, and he doesn't want to be changed."
6. He's less affectionate. Cheating men often forgo hand-holding, pecks on the cheek and snuggling on the couch—while still having sex with you. Sex can be just a physical act, while true intimacy is harder to fake. This may only be a pink flag, though, "if he's not the touchy-feely type or if he's stressed," cautions Nancy B. Irwin, PsyD, a therapist in Los Angeles. But if he's always been loving and you don't know why he'd be anxious, tell him you miss his touch and ask if something's wrong. "If he denies any change, then the pink flag's turned red," says Dr. Irwin.
7. He's got vices. Whether he drinks too much, dabbles in drugs or has a gambling problem, "he doesn't understand self-discipline, so he believes he can get away with things," notes Tina B. Tessina, PhD, author of Money, Sex and Kids: Stop Fighting about the Three Things That Can Ruin Your Marriage.Then there's this: Partiers by definition hang out—when their inhibitions have been lowered—where it's easy to pick up women. Your defense? "Take good emotional care of yourself, and stop pretending he's your knight in shining armor," says Dr. Tessina.
Tessina, PhD, author of Money, Sex and Kids: Stop Fighting about the Three Things That Can Ruin Your Marriage.Then there's this: Partiers by definition hang out—when their inhibitions have been lowered—where it's easy to pick up women. Your defense? "Take good emotional care of yourself, and stop pretending he's your knight in shining armor," says Dr. Tessina.
8. He's charming. And not just to your mother. If people often observe, "He could charm the pants off anyone!" he may be doing just that. We all start out figuring out how to circumvent rules, smiling at Mommy so she won't be mad that we threw our toys. But most men grow out of that. Unlike Anthony Weiner. "He does outrageous things that can ruin his career, then tries to charm his way out of it," notes Dr. Tessina. Her advice: "Keep him on notice that you will leave any time he's not holding up his end of the bargain. Respond positively when you're getting what you want from him, and don't react at all when you don't. "
"
9. He's powerful. Think Eliot Spitzer, Bill Clinton, Tiger Woods, Arnold Schwarzenegger and yes, Mr. Weiner. Studies show that men who perceive themselves as powerful are more likely to be unfaithful. "Power, it appears, can be a strong aphrodisiac and make men feel invincible," says Andee Harris, a certified life coach and founder of BedroomChemist.com. The best ways to keep your CEO or senior partner from straying is to stay physically connected, tell him how attracted you are to him and nag less often. If you think your efforts have failed, "confront him with whatever evidence you have, whether physical or circumstantial, and demand honesty," suggests Harris.
10. He's critical. "It's a cheater's way of manipulating you into doubting what you believe and questioning your rights," says Fran Walfish, PhD, a psychotherapist in Beverly Hills, CA. What better way to keep you from calling him on suspicious behavior than by making you second-guess yourself? Nitpicking is especially suspicious if he was never bothered by your weight, housekeeping habits or job before. If he shows no other signs of cheating, "tell him clearly how much hearing his feelings spoken in such a critical way hurts you," suggests Dr. Walfish. But if you feel pretty sure there's another woman, "approach your man with your hunch. If he owns up, shows genuine remorse and gets himself into therapy, there's hope. Staunch denial may mean you should go to a therapist to help you extract yourself from this toxic relationship," advises Dr. Walfish.
If he shows no other signs of cheating, "tell him clearly how much hearing his feelings spoken in such a critical way hurts you," suggests Dr. Walfish. But if you feel pretty sure there's another woman, "approach your man with your hunch. If he owns up, shows genuine remorse and gets himself into therapy, there's hope. Staunch denial may mean you should go to a therapist to help you extract yourself from this toxic relationship," advises Dr. Walfish.
detailed analysis. Scientific research, characteristics, tests and how to deal with it - Careers on vc.ru
There are many myths and opinions around the "impostor syndrome". Together with Elena Stankovskaya, Ph.D. in Psychology, a practicing consultant and teacher of the People Mindset practical online course, we analyzed in detail what this phenomenon is, whether it is necessary to fight it, and how it manifests itself in different people.
100 689 views
"Imposter Syndrome" is not a medical diagnosis, but rather a name for a set of experiences that are understandable and close to different people.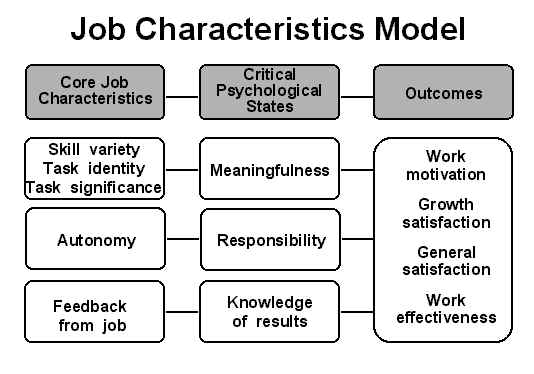 We recognize ourselves when we read about this "syndrome", although there is no single cause behind the list of manifestations. This is similar to a temperature or a runny nose - in themselves they are not some kind of disease and can occur from a sore throat, flu, acute respiratory infections, or something else.
We recognize ourselves when we read about this "syndrome", although there is no single cause behind the list of manifestations. This is similar to a temperature or a runny nose - in themselves they are not some kind of disease and can occur from a sore throat, flu, acute respiratory infections, or something else.
From the point of view of Soviet clinical psychology, a “syndrome” is a group of symptoms that naturally appear together due to a common operating cause. And the authors of the term believed that such a reason exists for the impostor syndrome, but later studies have refuted this opinion.
Now it is believed that although the "syndrome" reflects real experiences, there are very different mechanisms behind it - and therefore it is much more effective to work with these experiences separately than to separate them into a separate "syndrome". In this sense, the original term “imposter phenomenon” is more accurate - many people actually perceive their success as an accident and are afraid of exposure: they say that others will figure it out and understand that they do not correspond to their position or qualifications.
When clients come to me and complain about "Imposter Syndrome", I understand that this is their way of framing the problem. People come across articles about the "syndrome", and its description resonates, seems familiar and close. So I’m clarifying exactly how the “syndrome” manifests itself, what specifically worries people - because there are many reasons why we cannot appropriate success or are afraid of exposure. After I got acquainted with the client’s unique experience of “impostering”, we together try to understand what amplifies these experiences now, what events from the past have shaped them, and look for other ways to perceive ourselves.
Elena Stankovskaya
Scientists on "Imposter Syndrome"
1979 Paulina Klance and Susan Imes published "The Impostor Phenomenon Among High-Achieving Women", which pioneered the term "Imposter Syndrome". They studied women who achieved objective career success but still felt like cheaters. According to Clans and Imes, "Imposter Syndrome" is a kind of "internal experience of intellectual falsity" in people who cannot stomach their success. They concluded that the “syndrome” has six characteristics (more on these in the next section):
According to Clans and Imes, "Imposter Syndrome" is a kind of "internal experience of intellectual falsity" in people who cannot stomach their success. They concluded that the “syndrome” has six characteristics (more on these in the next section):
- Impostor cycle.
- The desire to be special or to be the best.
- An aspect of superman/superwoman.
- Fear of mistakes or failure.
- Denying one's own competence and ignoring praise.
- Fear and guilt for one's own success.
1985 Harvey and Katz defined "Imposter Syndrome" as "a psychological pattern rooted in a strong and hidden feeling of being a con artist when something needs to be achieved." According to them, the "impostor syndrome" should have three signs:
- Belief that you are deceiving other people.
- Fear of being exposed.
- Failure to recognize one's achievements, abilities, intelligence or qualifications.
1991 Colligian and Sternberg coined the term "perceived fraud" to avoid confusion between "Imposter Syndrome" and commonplace fraud. They didn't see impostor syndrome as an emotional disorder, but as a combination of cognitive and affective elements—that is, a fixed thought pattern.
2005 Kets de Vries studied the phenomenon of deception and included "Imposter Syndrome" in it. He considered cheating to be a social norm - after all, we must hide our weaknesses and stay within the generally accepted standards of behavior. According to Kets de Vries, going beyond this gives rise to two extremes: unethical deception (banal fraud) and neurotic deception (that is, the “impostor syndrome”). Consider what he understood by the norm and extremes.
- Norm. Each of us is an impostor, because we strive to conform to some ideas of others and demonstrate a public self that is different from our real ones.

- Real impostors. They display a false identity to deceive others and are satisfied when they succeed. Such people may have a real fear of exposure.
- Neurotic impostors. Their experience of cheating is subjective, meaning they don't do anything truly unacceptable. Such people feel like deceivers regardless of the opinion of outsiders. They are characterized by fear of failure or success, perfectionism, procrastination, workaholism.
All scientists' definitions agree on one thing: "the impostor syndrome" is the subjective psychological experience of a person who is afraid of exposure and is sure that he is a deceiver.
Elena Stankovskaya — Candidate of Sciences in Psychology, Consultant Psychologist, Associate Professor at the National Research University Higher School of Economics, author of the book Transactional Analysis: 7 Lectures for the Magisteria Project. She leads the Imposter Syndrome module in the People Mindset Leadership module, a hands-on online course on teamwork and leadership skills.
It starts October 5th.
Characteristics of "Imposter Syndrome" according to Clans and Imes
Paulina Klance states that if a person has at least two of these characteristics, he is subject to the "Imposter Syndrome". Let's analyze them in more detail.
Imposter Cycle
The impostor cycle begins when a person is faced with the need to achieve something - for example, study or a project at work:
- Anxiety arises in a person.
- Anxiety provokes either overpreparation or procrastination. Moreover, procrastination is followed by a stage of intense “doing” - after all, you have to meet the deadline.
- When the task is ready, there is a sense of relief and accomplishment. But this feeling passes quickly.
- People around give positive feedback, but the person does not accept it, because it does not correspond to his perception of the mechanism of success, and does not believe that success is related to his abilities.
- If the second stage was overpreparation, the person believes that success is due to hard work. If there was procrastination in the second stage, then he explains the success as random luck. At the same time, a person firmly believes that achieving a result through hard work does not confirm his abilities.
- Then the person is faced with a new challenge, self-doubt causes anxiety and the impostor cycle repeats.
The impostor cycle has two permanent effects - overload and increased sense of fraud.
Overload. Occurs due to the fact that the efforts and energy spent on achieving the goal significantly exceed the necessary ones and interfere with other priorities. Moreover, people with the "impostor syndrome" are aware of this problem, but in practice they almost never can break this pattern of behavior and limit themselves only to the necessary efforts.
Increasing sense of fraud from cycle to cycle. Paradox: every time the success is repeated, the "impostor syndrome" only gets worse. Paulina Klance suggested that the "imposters" have their own ideal of success and excessive expectations from the goals achieved. They simply ignore their accomplishments if the actual performance falls short of their ideal standard. At the same time, “imposters” are high achievers who unreasonably rate their work low, which means that each achievement further emphasizes the gap between real and imagined standards of success, reinforcing the “imposter syndrome”.
Imposter Cycle - from "The Impostor Phenomenon", Jaruwan Sakulku, James Alexander
The need to be special, the best
Often people with "Imposter Syndrome" secretly want to be better than their peers or colleagues. All their childhood they could be the first in the class or school, but when they come to the university or get a job, they understand that there are many outstanding people in the world, and their talents are not phenomenal. As a result, "imposters" simply ignore their abilities and conclude that they are simply stupid.
As a result, "imposters" simply ignore their abilities and conclude that they are simply stupid.
Superwoman/Superman Aspects
This item is closely related to the previous one. People with Imposter Syndrome demand perfection from themselves in all areas of life. They set themselves almost unattainable standards, and then feel overwhelmed and disappointed.
Fear of failure
"Imposters" are very worried when it is necessary to achieve something - they are terribly afraid of failure. Making mistakes or not doing everything to the highest standard, they feel shame and humiliation. For most people with Imposter Syndrome, it is fear that becomes the main driver. Result: They try to reduce the risk of failure and start working too hard.
Feeling incompetent and underestimating praise
People with "Imposter Syndrome" cannot accept compliments and believe in themselves, they tend to attribute success to external factors, ignore positive reviews and objective indicators of success. Not only that, they are making efforts to prove to everyone: we do not deserve praise, this is not our achievement. But "Imposter Syndrome" is a much deeper and more serious phenomenon than coquetry or false modesty.
Not only that, they are making efforts to prove to everyone: we do not deserve praise, this is not our achievement. But "Imposter Syndrome" is a much deeper and more serious phenomenon than coquetry or false modesty.
Fear and guilt about success
"Imposters" often feel guilty about being different from others or doing better than those around them - they are very afraid of being rejected. Another of their fears is excessive demands or expectations from others. "Imposters" are not confident that they can maintain their level of efficiency and refuse additional responsibility, and excessive demands or expectations can "reveal" their "deception".
When and why to go to a psychologist
If you have found in yourself at least two of the characteristics from the last chapter, then you have an "impostor syndrome". But it is not always necessary to get rid of it - only if the "syndrome" interferes with living or building a career.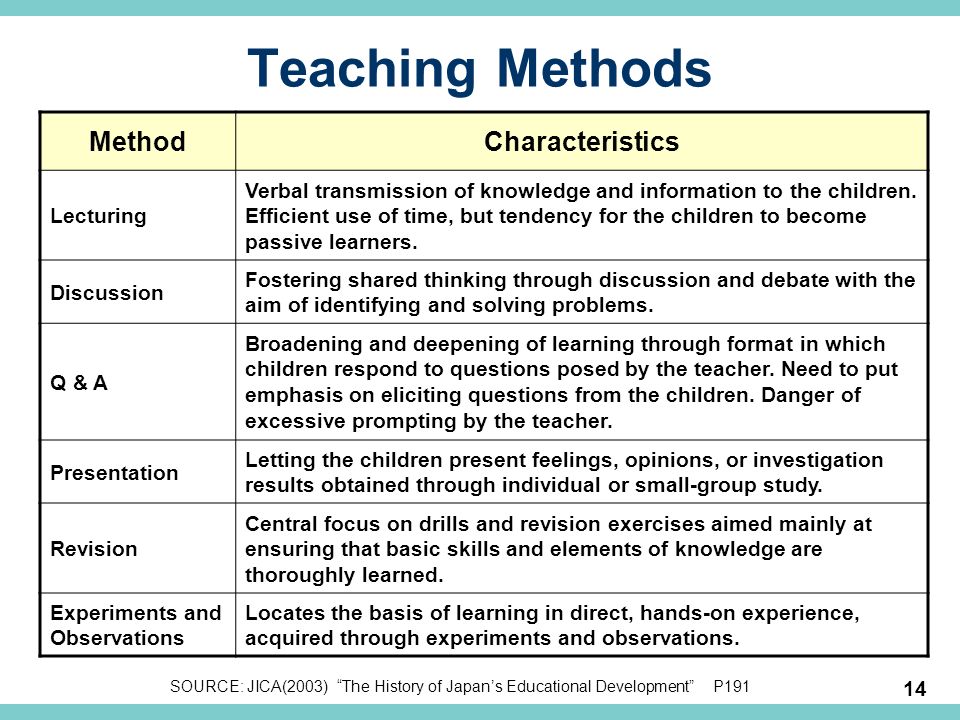 As a first approximation, this is easy to understand:
As a first approximation, this is easy to understand:
- Career. A person does not pretend to what he could get and what he deserves - it seems to him that they are deceiving everyone even in their current position. Although in fact he has qualities that would benefit the company in a higher position.
- Quality of life. Most of the energy and nerves are spent not on doing the job, but on avoiding exposure, over-preparing for projects, internal struggles and servicing their doubts.
Paulina Klance has developed a test that helps determine the degree of development of "Imposter Syndrome".
"Imposters" often choose some kind of role model for themselves - the very image of a "smart brother" or "smart sister" that they aspire to. Moreover, it can be both a living person and a historical figure, as in Mayakovsky's "Letter to Comrade Kostrov":
.
.. break loose,
jealous of Copernicus,
him,
and not Marya Ivanna's husband,
considering
his rival
.
But even if a person with "Imposter Syndrome" achieves his goals and objectively outgrows this ideal image, he will not get rid of problems, but will continue to spend energy on fighting fear and doubt. In this case, there can be two scenarios:
- We do not notice at all that we have outgrown our role model, and imperceptibly we switch to comparison with the new Copernicus.
- We say that we were just lucky, it's just a case, luck, or colleagues and relatives helped us in time, and we continue to consider this person better than ourselves.
As a result, the life scenario does not change, but a distorted perception appears: we take only those facts that confirm our idea of ourselves. And a mental system is built that supports itself with all its might, ignoring the facts that contradict it.
Another reason to tackle this topic is the avoidance behavior that underlies the "Imposter Syndrome". If you often choose an activity that helps to hide that you don’t know something, refuse new heights, self-expression, hide your thoughts because of fear, this is an occasion to reconsider your ideas about yourself. Having dealt with all this, we get more freedom - we can choose activities not out of fear, but based on what turns us on and what we really want.
The basis of the "syndrome" is an internal conflict
The impostor syndrome is paradoxical: I feel like a deceiver, but at the same time I know that I am not, it is just a "syndrome". That is, some part of me believes in my strength and that I receive recognition deservedly.
Consider an example: a woman works in a male team, in a position that is traditionally considered “male” in society. And they certainly face a negative attitude towards themselves, depreciation of their work, distrust. Such an attitude of others reinforces internal doubts about competence, but a woman does not quit, moreover, she strives to grow and build a career. Thus, under these doubts, inner confidence is almost always hidden - no, after all, I am smart, capable. I attribute my success to chance, and at the same time I think that when I do this, it's a "syndrome".
Such an attitude of others reinforces internal doubts about competence, but a woman does not quit, moreover, she strives to grow and build a career. Thus, under these doubts, inner confidence is almost always hidden - no, after all, I am smart, capable. I attribute my success to chance, and at the same time I think that when I do this, it's a "syndrome".
As a result, "Imposter Syndrome" is not some kind of total insecurity, but a constant tension between confidence and doubts about one's abilities. After all, if a person is sincerely sure of his incompetence, then why should he achieve something? He will live quietly at his level and will not strive for something great.
And there may be different causes and manifestations. Many people have the illusion that if they were truly smart, then everything would work out very easily for them - and in any area. Roughly speaking, if a person from year to year cannot master some narrow part of his work, then he gets the feeling that in other areas he is a complete zero. The stereotyped idea that truly smart people do everything almost intuitively is to blame for this: they get behind the wheel and immediately know how to drive a car. And if you have to “squirm” at the circuit for 20 hours in a row, then you are definitely an impostor and a deceiver.
The stereotyped idea that truly smart people do everything almost intuitively is to blame for this: they get behind the wheel and immediately know how to drive a car. And if you have to “squirm” at the circuit for 20 hours in a row, then you are definitely an impostor and a deceiver.
There is also a second frequent manifestation: it is impossible to show that I am proud of myself, that I am cool or cool. And here the reason may be hidden in childhood, when a pattern of behavior is imposed on the child: do not stick out, do not attract attention, do not show your success, sit silently and quietly, hide. There are also more individual cases.
We write about product management and development in the make sense and Product Mindset telegram channels, and you can discuss any product issues in Product Sense Chat.
For example, a talented and bright student transfers to another school, and there his talents are not appreciated and there is no opportunity to show them - they are simply of no interest to anyone. And when in the future some “strange” people come to him and say: you are very smart, cool, you are doing great, he cannot believe them, because he has already formed a strong opinion about himself.
And when in the future some “strange” people come to him and say: you are very smart, cool, you are doing great, he cannot believe them, because he has already formed a strong opinion about himself.
It turns out that the core of the "impostor syndrome" is script beliefs and basic ideas about ourselves, as well as how others perceive us. And even if I have accumulated a large collection of external achievements, my strong inner conviction is no longer disputed. Because scenario beliefs support our picture of the world, stabilize it, shape the perception of reality. A simple example: if I was a black sheep at school - smarter and more talented than others, and therefore they told me all the time that I was not ok, then when people suddenly start praising me, then my patterns do not allow this praise to be digested and I think they are wrong or some weird ones.
Causes of the "Imposter Syndrome"
"Imposter Syndrome" is a popular subject of research, but scientists are still arguing about the reasons for its appearance. Some point to the influence of the family atmosphere in childhood, others emphasize the importance of character traits such as neuroticism, and still others explore the problems of minorities in work teams - national, gender, racial, social.
Some point to the influence of the family atmosphere in childhood, others emphasize the importance of character traits such as neuroticism, and still others explore the problems of minorities in work teams - national, gender, racial, social.
Paulina Klance and Susan Imes found two typical scenarios in the childhood of women with "Imposter Syndrome":
- A smart brother or sister, with whom they were constantly compared and to whom they have been trying to grow up all their lives, to prove to everyone that they are also worth something.
- As children, they were praised a lot and told that they could overcome any obstacles with their abilities. But as they grew up, they understood: much is given to them with difficulty, which means that they are not as good as everyone thought.
In 2006, Julie Vaunt and Sabina Kleitman conducted a study and found out an interesting fact: the fears of "imposters" are very much dependent on excessive care and custody from the father, and the mother's parenting style affects them only indirectly - as a reflection of the father's style.
Another “syndrome” arises because of the cult of intellect in the family — and then the “imposters” do their best to change their behavior, meet the family's standards and please their parents in order to keep or earn their love. Even to the detriment of their nature and desires. If the family does not give support and approval to the child, he thinks that his achievements are not interesting or impressive to anyone. And then there is shame, a feeling of humiliation and a feeling - I am an impostor.
"Imposter Syndrome" is also associated with the Dunning-Kruger effect, when low-skilled people overestimate their abilities, while professionals tend to doubt their abilities, feel insecure and consider others more competent. As in the story about Socrates: he proved to his students that he did not know much more than they did. Socrates drew two circles - the small one showed the amount of knowledge of the students, the large one - his own knowledge. The zone of the unknown is that which is in contact with the circle, which means that Socrates does not know much more than his students.
The Dunning-Kruger effect is also correlated with research by Jim Collins, which formed the basis of the book Good to Great. Collins speaks of five levels of leaders, of which we are only interested in levels four and five, the highest levels of leadership development.
- The manager of the fourth level attributes all the achievements of the company to himself, his qualities and insight, and they tend to shift the responsibility for failures to others. For such a leader, success is a natural consequence of his own talent, he is confident in himself, knows how to speak brightly and motivate the team.
- Level 5 leaders almost always say “we”, “just lucky”, “there were very talented people in the team”. Such leaders outwardly look uncertain and modest, they look for the reasons for failures in their decisions and actions, they motivate by their own example, and not by incendiary speeches. At the same time, they have a strong will and desire to succeed.
 Long-term success for companies is usually driven by Level 5 leaders.
Long-term success for companies is usually driven by Level 5 leaders.
Who is subject to "Imposter Syndrome"
Klance and Aimes considered the "Imposter Syndrome" to be a social phenomenon: successful women were much more likely than their male counterparts to believe that their success was accidental, and those around them would never give them grants and recognition if they understood the situation better. At first, the authors associated the "syndrome" with social inequality, discrimination, and the position of women at that time - women were not considered capable of leading or achieving anything serious outside the household.
But in 1993, after a series of studies, Pauline Klance confirmed that men also often become victims of the “impostor syndrome”. In general, up to 70% of people go through this “syndrome” at least once in their lives (The Impostor Phenomenon), among which there are many successful and famous people. Michelle Obama, Tom Hanks, famous writer John Steinbeck, actress Jodie Foster, and even Einstein shared their feelings about the "Imposter Syndrome" at various times.
Michelle Obama, Tom Hanks, famous writer John Steinbeck, actress Jodie Foster, and even Einstein shared their feelings about the "Imposter Syndrome" at various times.
Types of "imposters"
Manifestations of "Imposter Syndrome" vary from person to person. For example, a “narcissist” considers himself exceptional and is afraid that others will suddenly figure him out and say: you are ordinary, like all of us. And an anxious person will not be able to establish himself in some kind of positive opinion about himself and will each time try to build it anew.
Valerie Young, an expert on "imposters", created a classification of people subject to this "syndrome".
- Perfectionists. They set themselves an overstated bar, and then even if they achieve goals by 99% feel like failures. Any mistake - and they doubt their competence.
- "Experts". They constantly go to trainings and accumulate certificates, trying to get too detailed information before starting any project.
 They are afraid of looking stupid, so they are embarrassed to ask questions in meetings or in class. They will not take on the project if they do not meet all the formal criteria specified in the requirements.
They are afraid of looking stupid, so they are embarrassed to ask questions in meetings or in class. They will not take on the project if they do not meet all the formal criteria specified in the requirements. - "Natural Geniuses". They got used to the fact that everything was easy for them in their childhood. Therefore, when you have to work hard to achieve a goal, they consider it a sign of their incompetence.
- Soloists. They feel that they are obliged to do everything on their own, and asking for help means signing their insolvency.
- "Supermen" / "Superwoman". Force themselves to work harder than others to prove their level. Trying to succeed in all areas of life - at work, in the family, in relationships - and can experience severe stress when something does not work out.
Development driver and stable worldview
There are pluses in the "impostor syndrome" - it stabilizes the picture of the world, structures our activity and time. Yes, we doubt, but we have a stable understanding - I am a deceiver and I know that I should be afraid of being exposed. This is a very stable and predictable picture of the world. But when we are told: you are doing everything great - we are lost and do not know what to believe, this creates a conflict with our picture of the world and we say: no, this is how I am and this is what I should be afraid of.
Yes, we doubt, but we have a stable understanding - I am a deceiver and I know that I should be afraid of being exposed. This is a very stable and predictable picture of the world. But when we are told: you are doing everything great - we are lost and do not know what to believe, this creates a conflict with our picture of the world and we say: no, this is how I am and this is what I should be afraid of.
Because of the "Imposter Syndrome", people invest a lot of time in their studies and work, in developing their professional skills. And then our "syndrome" becomes a driver of personal development. Behind this process is the desire to realize our inner conviction that we are smart and talented after all. As a result, a person really does a lot of work, pumping much more intensively and deeper than those who do not consider themselves a deceiver. And although subjectively the “imposter” cannot appropriate success for himself, but objectively, deep inside, he understands that this is true, I did it. And this understanding gives a certain happiness.
And this understanding gives a certain happiness.
Strategies for dealing with "Imposter Syndrome"
There are two ways to get rid of the vivid manifestations of the "impostor syndrome": with the help of quality feedback, a psychologist, or on your own.
Feedback. Despite the stable picture of the world of "impostors", the development of the "syndrome" depends very much on the quality of the feedback. When there is strong, supportive and realistic feedback, a person gradually develops an adequate self-image.
We recommend two episodes of the make sense podcast about team relationships: About conflicts and difficult situations in a team, and about the role of emotions and trust in relationships with Andrey Ryzhkin, About company culture and values, remote work and mental health with Anna Boyarkina
Psychologist. Turning to a psychologist and understanding with him why the “syndrome” has formed and what to do with it is a good method.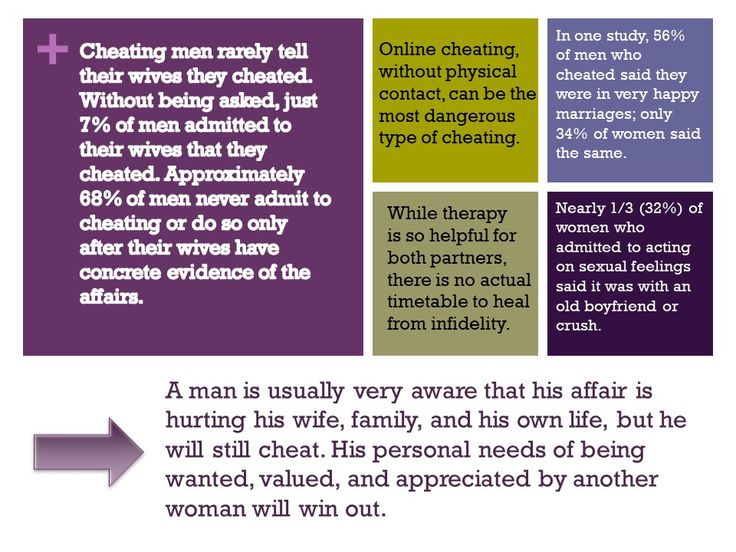 Together with a specialist, you can go from the present to the past and answer important questions:
Together with a specialist, you can go from the present to the past and answer important questions:
- What is supporting these doubts right now?
- Are there people who believe in my client's competence and talent?
- What kind of feedback does he get and what accomplishments can he really be proud of?
- Why does he think that these achievements do not belong to him?
- What is the use of doubt?
- Who does the client consider smart and talented, who does he look up to? Where did this level of ambition come from?
Then you can go into the past and understand how and when the “impostor syndrome” was formed:
- In what relationship did this feeling and self-image arise?
- What experience fixed the "syndrome", and what - vice versa?
- How does the client now confirm his competence and what gives him?
If you passed the Paulina Clans test and it showed a very high level of development of the "impostor syndrome", you should contact a specialist - he will help you make the "syndrome" your friend and growth driver, and not a development blocker that enslaves and prevents you from realizing yourself.
How to properly communicate with those who are prone to impostor syndrome, build healthy relationships with the team and the world around it, be a leader who helps others grow and grow yourself through it, as well as how to better understand your strengths and weaknesses and use it for development , we analyze in detail on the People Mindset course together with teachers from Miro, Vyshka, CIAN, Skyeng and other leading companies.
Alaina Levin's Advice: How to Deal with Impostor Syndrome on Your Own
Alaina is a STEM career consultant and author of Networking for Nerds (Wiley, 2015).
You are the driver. "Imposter Syndrome" is just a fantasy. It is based only on your opinion, not facts. It is a subjective internal, not an objective external process. But you manage yourself, and therefore, you can quite fight the “syndrome”. This will give strength.
Don't hide from your emotions. You may experience insecurity, fear, shame, anxiety, and other negative emotions during your "fits" of impostor syndrome. But that's okay - allow yourself to experience them and write down how you feel. This will help you understand how impostor syndrome affects you, and in the future you will already clearly understand when it manifests itself.
You may experience insecurity, fear, shame, anxiety, and other negative emotions during your "fits" of impostor syndrome. But that's okay - allow yourself to experience them and write down how you feel. This will help you understand how impostor syndrome affects you, and in the future you will already clearly understand when it manifests itself.
Get angry! But not on yourself: “Who does this syndrome think it is? And why the hell is he whispering to me that I'm unworthy of my position? Let's get out of here!" Giving vent to your anger, you understand: no one will convince you that you are in the wrong place.
Review your professional experience. Remember all the completed projects, skills, interesting solutions to work problems, review your presentations, documents. These are your real achievements, facts, not fantasies. Such a review will help to counter the subjective “arguments” that the “syndrome” palms off.
Try to prove that you are an impostor. When you've done a review, ask yourself why you're objectively unfit for the position or an impostor. When you have collected such facts, note those that are associated with emotions. You will see, you will have almost no real arguments left.
When you've done a review, ask yourself why you're objectively unfit for the position or an impostor. When you have collected such facts, note those that are associated with emotions. You will see, you will have almost no real arguments left.
Look around. Who else has achieved such success? Did they have the same “necessary” training that you are supposedly required to have? If they are successful, then so can you.
Keep moving forward. Constantly take small steps that will demonstrate in a moment that you are not an impostor and help you move up the career ladder. Publish an article, do a little research, agree on cooperation with an interesting person. Also, try incorporating flow state into your work.
Be kind to yourself. It takes resilience, flexibility, and courage to beat the impostor syndrome. Constantly remind yourself that I am not a fraud and would never have received such a position and responsibility if I was stupid. Praise yourself when you manage to calm the manifestations of the “syndrome”. But remember - he can come back at any moment. So relax and if necessary return to the first point - act iteratively, over time it will get better and better.
Praise yourself when you manage to calm the manifestations of the “syndrome”. But remember - he can come back at any moment. So relax and if necessary return to the first point - act iteratively, over time it will get better and better.
Contact support
It seems that everything is simple, but science has again made its corrections. In 2019, a group of scientists published a study on "Imposter Syndrome". It turns out that it is very important to ask for support outside of the area in which you feel like an "imposter". Doing Data Science? Seek support from your grandmother, brother, accountants or PR friends. Do you work in marketing? Contact turners, logisticians and managers. Outsiders often see our competence better and are able to assess our knowledge and skills.
In the sources you will find several more effective methods to combat the "imposter syndrome", but they will not work if you really are an impostor - it happens :) These methods have another limitation: they are able to contain the syndrome, but do not cure his. And if the “impostor syndrome” is highly developed, you still have to figure out its causes together with a specialist.
And if the “impostor syndrome” is highly developed, you still have to figure out its causes together with a specialist.
References
- The imposter phenomenon in high achieving women: Dynamics and therapeutic intervention, Pauline Rose Clance, Suzanne Ament Imes
- A validation study of the Harvey Impostor Phenomenon Scale, Edwards, P. W., Zeichner
- Yes, Impostor Syndrome Is Real. Here's How to Deal With It
- The Impostor Phenomenon, Jaruwan Sakulku, James Alexander
- Imposter phenomenon and self-handicapping: Links with parenting styles and self-confidence
- When Will They Blow My Cove?: The Impostor Phenomenon Among Austrian Doctoral Students
- Impostor phenomenon and mental health: The influence of racial discrimination and gender
- Impostor feelings as a moderator and mediator of the relationship between perceived discrimination and mental health among racial/ethnic minority college students
- Good to Great by Jim Collins
- Lecture notes by Ludwig Bystronovsky on how to develop in the profession
- How to banish impostor syndrome, Alaina G.
 Levine
Levine - 10 steps you can use to overcome impostor syndrome, Valerie Young
- "I must have slipped through the cracks somehow": An examination of coping with perceived impostorism and the role of social support, Journal of Vocational Behavior, Volume 115, December 2019, 103337
- Thinking your way out of imposter syndrome, Valerie Young on TEDx
- Impostor Syndrome: 5 Ways To Overcome It and Thrive, Vanessa Van Edwards
- If You Struggle With Imposter Syndrome, Scientists Might Have an Odd Solution, Peter Dockrill
Face Anti-Spoofing or technologically recognize a deceiver from a thousand by face / Sudo Null IT News Passwords can be stolen, spyed, forgotten, keys can be faked. But the unique characteristics of the person himself are much more difficult to fake and lose. These can be fingerprints, voice, pattern of retinal vessels, gait, and so on.

Of course biometric systems are trying to cheat! That's what we'll talk about today. How attackers try to bypass facial recognition systems by impersonating another person and how this can be detected.
A video version of this story can be viewed here, and for those who prefer reading to watching, I invite you to follow along. You just need to show the system the "required parts" of the real user, both individually and taking him hostage as a whole. Or you can “put on the mask” of another person on yourself, for example, with the help of a physical transplant of a mask or in general, the presentation of false genetic traits
In real life, attackers also try to pretend to be someone else. For example, rob a bank while wearing the mask of a black man, as in the picture below.
Face recognition looks like a very promising area for use in the mobile sector. If everyone has long been accustomed to using fingerprints, and voice technologies are gradually and rather predictably developing, then the situation with facial identification is quite unusual and worthy of a short digression into the history of the issue.
How it all began, or from fantasy to reality
Today's recognition systems demonstrate tremendous accuracy. With the advent of large data sets and complex architectures, it has become possible to achieve face recognition accuracy up to 0.000001 (one error in a million!) And they are already suitable for porting to mobile platforms. The bottleneck was their vulnerability.
In order to impersonate another person in our technical reality, and not in the film, masks are most often used. They also try to fool the computer system by presenting someone else's face instead of their own. Masks come in a wide variety of qualities, from a printed photo of another person held in front of your face, to very complex heated 3D masks. Masks can either be presented separately in the form of a sheet or screen, or put on the head.
A successful attempt to trick the iPhone X's Face ID system with a rather elaborate rock powder mask with special eye pads that simulate the heat of a living face using infrared radiation has attracted a lot of attention.
It is claimed that using such a mask it was possible to deceive Face ID on the iPhone X. Video and some text can be found here .
Terminology
The field of face anti-spoofing research is quite new and can't even boast of established terminology yet.
Let's agree to call an attempt to deceive the identification system by presenting it with a fake biometric parameter (in this case, a face) spoofing attack .
Accordingly, a set of protective measures to counter such deception will be called anti-spoofing . It can be implemented in the form of a variety of technologies and algorithms that are built into the pipeline of the identification system.
ISO offers a somewhat extended set of terminology, with terms such as presentation attack - attempts to force the system to misidentify a user or allow him to avoid identification, by showing a picture, recorded video, and so on. Normal (Bona Fide) - corresponds to the normal algorithm of the system, that is, everything that is NOT an attack. Presentation attack instrument means a means of attack, such as an artificial body part. And finally Presentation attack detection - automated means of detecting such attacks. However, the standards themselves are still in development, so it is impossible to talk about any established concepts. Terminology in Russian is almost completely absent.
Normal (Bona Fide) - corresponds to the normal algorithm of the system, that is, everything that is NOT an attack. Presentation attack instrument means a means of attack, such as an artificial body part. And finally Presentation attack detection - automated means of detecting such attacks. However, the standards themselves are still in development, so it is impossible to talk about any established concepts. Terminology in Russian is almost completely absent.
To determine the quality of the system, the metric HTER (Half-Total Error Rate - half of the total error) is often used, which is calculated as the sum of the coefficients of erroneously allowed identifications (FAR - False Acceptance Rate) and erroneously forbidden identifications (FRR - False Rejection Rate) divided in half.
HTER=(FAR+FRR)/2
It is worth saying that in biometric systems, FAR is usually given the most attention, in order to do everything possible to prevent an intruder from entering the system. And they are doing quite well (remember the one in a million from the beginning of the article?) The downside is the inevitable increase in FRR - the number of ordinary users erroneously classified as intruders. If for government, defense and other similar systems this can be sacrificed, then mobile technologies, working with their huge scale, variety of subscriber devices and, in general, user-perspective oriented, are very sensitive to any factors that can force users to refuse services. If you want to reduce the number of phones smashed against the wall after the tenth consecutive failure of identification, you should pay attention to FRR!
And they are doing quite well (remember the one in a million from the beginning of the article?) The downside is the inevitable increase in FRR - the number of ordinary users erroneously classified as intruders. If for government, defense and other similar systems this can be sacrificed, then mobile technologies, working with their huge scale, variety of subscriber devices and, in general, user-perspective oriented, are very sensitive to any factors that can force users to refuse services. If you want to reduce the number of phones smashed against the wall after the tenth consecutive failure of identification, you should pay attention to FRR!
Types of attacks. We deceive the system
Let's finally find out exactly how attackers deceive recognition systems, and also how this can be countered.
The most popular means of deception are masks. There is nothing more obvious than putting on a mask of another person and presenting the face to an identification system (often referred to as a Mask attack).
You can also print a photo of yourself or someone else on a piece of paper and hold it up to the camera (let's call this type of attack a Printed attack).
Slightly more complex is the Replay attack, when the system is presented with the screen of another device, which plays a pre-recorded video with another person. The complexity of execution is compensated by the high efficiency of such an attack, since control systems often use signs based on the analysis of time sequences, for example, tracking blinking, micro-movements of the head, the presence of facial expressions, breathing, and so on. All this can be easily reproduced on video.
Both types of attacks have a number of characteristic features that allow them to be detected and, thus, to distinguish the screen of a tablet or sheet of paper from a real person.
Let's summarize the characteristic features that allow us to identify these two types of attacks in a table:
Printed attack | Replay attack | |
|---|---|
| Decreased image texture quality when printing | Moire |
| Halftone artifacts when printing on | printerReflections (glare) |
| Mechanical printing artifacts (horizontal lines) | Flat picture (no depth) |
Absence of local movements (e. g. blinking) g. blinking) | Image borders may be visible |
| Image borders may be visible |
Attack detection algorithms. Good old classic
One of the oldest approaches (works of 2007, 2008) is based on the detection of human blinks by analyzing the image using a mask. The point is to build some kind of binary classifier that allows you to select images with open and closed eyes in a sequence of frames. This can be the analysis of a video stream using the selection of parts of the face (landmark detection), or the use of some simple neural network. And today this method is most often used; the user is prompted to perform some sequence of actions: turn his head, wink, smile, and so on. If the sequence is random, it is not easy for an attacker to prepare for it in advance. Unfortunately, for an honest user, this quest is also not always surmountable, and engagement drops sharply.
You can also take advantage of the picture degradation features when printing or playing on the screen. Most likely, even some local patterns will be found in the image, albeit elusive to the eye. This can be done, for example, by counting local binary patterns (LBP, local binary pattern) for different areas of the face after selecting it from the frame (PDF). The described system can be considered the founder of the entire direction of face anti-spoofing algorithms based on image analysis. In a nutshell, when calculating LBP, each pixel of the image, eight of its neighbors, are sequentially taken and their intensity is compared. If the intensity is greater than on the central pixel, one is assigned, if less - zero. Thus, for each pixel, an 8-bit sequence is obtained. Based on the obtained sequences, a pixel-by-pixel histogram is constructed, which is fed to the input of the SVM classifier.
Most likely, even some local patterns will be found in the image, albeit elusive to the eye. This can be done, for example, by counting local binary patterns (LBP, local binary pattern) for different areas of the face after selecting it from the frame (PDF). The described system can be considered the founder of the entire direction of face anti-spoofing algorithms based on image analysis. In a nutshell, when calculating LBP, each pixel of the image, eight of its neighbors, are sequentially taken and their intensity is compared. If the intensity is greater than on the central pixel, one is assigned, if less - zero. Thus, for each pixel, an 8-bit sequence is obtained. Based on the obtained sequences, a pixel-by-pixel histogram is constructed, which is fed to the input of the SVM classifier.
Local binary patterns, histograms and SVM. You can join the timeless classic at the link
The HTER efficiency indicator is “as much as” 15%, which means that a significant part of the attackers overcome the protection without much effort, although it should be recognized that many are eliminated. The algorithm was tested on the Replay-Attack dataset from IDIAP, which is composed of 1200 short videos of 50 respondents and three types of attacks - printed attack, mobile attack, high-definition attack.
The algorithm was tested on the Replay-Attack dataset from IDIAP, which is composed of 1200 short videos of 50 respondents and three types of attacks - printed attack, mobile attack, high-definition attack.
Ideas for image texture analysis have been continued. In 2015, Bookinafit developed an algorithm for alternative channeling of an image into channels, in addition to the traditional RGB, for the results of which local binary patterns were again calculated, which, as in the previous method, were fed to the input of the SVN classifier. The accuracy of HTER, calculated on the CASIA and Replay-Attack datasets, was an impressive 3% at that time.
At the same time, work on the detection of moiré appeared. Patel published an article where he suggested looking for image artifacts in the form of a periodic pattern caused by the superposition of two scans. The approach proved to be workable, showing an HTER of around 6% on the IDIAP, CASIA, and RAFS datasets. It was also the first attempt to compare the performance of the algorithm on different datasets.
Periodic pattern on the image caused by superposition of scans
To detect attempts to present a photo, it was a logical decision to try to analyze not one image, but their sequence taken from the video stream. For example, Anjos and colleagues proposed to extract features from the optical stream on adjacent pairs of frames, feed them to the input of a binary classifier, and average the results. The approach proved to be quite effective, demonstrating an HTER of 1.52% on their own dataset.
An interesting method of tracking movements, which is somewhat away from the generally accepted approaches. Since in 2013 the principle of “feeding a raw image to the input of a convolutional network and adjusting the layers of the mesh until the result” was not common for modern deep learning projects, Bharadwazh successively applied more complex preliminary transformations. In particular, he applied the Eulerian video magnification algorithm, known from the work of scientists from MIT, which was successfully used to analyze color changes in the skin depending on the pulse. I replaced LBP with HOOF (optical flow direction histograms), correctly noting that as soon as we want to track movements, we need appropriate features, and not just texture analysis. The same SVM, traditional at that time, was used as a classifier. The algorithm showed extremely impressive results on the Print Attack (0%) and Replay Attack (1.25%) datasets
I replaced LBP with HOOF (optical flow direction histograms), correctly noting that as soon as we want to track movements, we need appropriate features, and not just texture analysis. The same SVM, traditional at that time, was used as a classifier. The algorithm showed extremely impressive results on the Print Attack (0%) and Replay Attack (1.25%) datasets
Let's learn grids already!
At some point, it became obvious that the transition to deep learning was overdue. The notorious “deep learning revolution” has overtaken face anti-spoofing.
The "first sign" can be considered a method of analyzing depth maps in separate areas ("patches") of the image. Obviously, the depth map is a very good indication of the plane in which the image is located. If only because the image on a sheet of paper has no "depth" by definition. In Ataum's 2017 work, many separate small areas were extracted from the image, depth maps were calculated for them, which were then merged with the depth map of the main image. At the same time, it was indicated that ten random patches of the face image are enough to reliably determine the Printed Attack. Additionally, the authors merged together the results of two convolutional neural networks, the first of which calculated depth maps for patches, and the second for the image as a whole. When training on data sets, a depth map equal to zero was associated with the Printed Attack class, and a series of randomly selected areas was associated with a three-dimensional face model. By and large, the depth map itself was not so important, only some indicator function was used from it, characterizing the “depth of the site”. The algorithm showed an HTER value of 3.78%. Three public datasets were used for training - CASIA-MFSD, MSU-USSA and Replay-Attack.
At the same time, it was indicated that ten random patches of the face image are enough to reliably determine the Printed Attack. Additionally, the authors merged together the results of two convolutional neural networks, the first of which calculated depth maps for patches, and the second for the image as a whole. When training on data sets, a depth map equal to zero was associated with the Printed Attack class, and a series of randomly selected areas was associated with a three-dimensional face model. By and large, the depth map itself was not so important, only some indicator function was used from it, characterizing the “depth of the site”. The algorithm showed an HTER value of 3.78%. Three public datasets were used for training - CASIA-MFSD, MSU-USSA and Replay-Attack.
Unfortunately, the availability of a large number of excellent deep learning frameworks has led to the emergence of a huge number of developers who are trying to solve the problem of face anti-spoofing in the well-known way of neural network ensembles. This usually looks like a stack of feature maps at the outputs of several networks, pre-trained on some widely used dataset, which is fed to a binary classifier.
This usually looks like a stack of feature maps at the outputs of several networks, pre-trained on some widely used dataset, which is fed to a binary classifier.
In general, it should be concluded that by now quite a lot of papers have been published, which generally demonstrate good results, and which are united by only one small “but”. All these results are demonstrated within one specific dataset! The situation is aggravated by the limited availability of data sets and, for example, the notorious Replay-Attack will not surprise anyone with HTER 0%. All this leads to the emergence of very complex architectures, for example, these, using various tricky features, auxiliary algorithms, stacked, with several classifiers, the results of which are averaged, and so on ... As a result, the authors get HTER = 0.04%!
This suggests that the task of face anti-spoofing within a particular dataset has been solved. Let's summarize in a table various modern methods based on neural networks. As you can easily see, the "reference results" were achieved by a wide variety of methods that only arose in the inquisitive minds of developers.
As you can easily see, the "reference results" were achieved by a wide variety of methods that only arose in the inquisitive minds of developers.
Comparative results of different algorithms. The table is taken from here.
Unfortunately, the blissful picture of the struggle for tenths of a percent is disturbed by the same "small" factor. If you try to train a neural network on one data set, and apply it on another, then the results will turn out to be ... not so optimistic. Worse, attempts to apply classifiers in real life do not leave any hope at all.
For example, let's take the data of the work of 2015, where the metric of its quality was used to determine the authenticity of the presented image. Take a look for yourself:
In other words, an algorithm trained on Idiap data and applied on MSU will give a true positive detection rate of 90.5%, but if you do the opposite (train on MSU, and check on Idiap), then only 47.2%(!) can be determined correctly (!) For other combinations, the situation worsens even more, and, for example, if you train the algorithm on MSU and check it on CASIA, then the TPR will be 10. 8%! This means that a huge number of honest users were erroneously classified as attackers, which is depressing. The situation could not be reversed even by cross-database training, which seems to be quite a reasonable way out.
8%! This means that a huge number of honest users were erroneously classified as attackers, which is depressing. The situation could not be reversed even by cross-database training, which seems to be quite a reasonable way out.
Let's see again. The results reported in Patel's 2016 paper show that even with fairly complex processing pipelines and robust feature extraction such as blinking and texture, the results on unfamiliar datasets cannot be considered satisfactory. So, at some point it became quite obvious that the proposed methods are desperately lacking to generalize the results.
And if we organize a competition…
Of course, in the field of face anti-spoofing there were some competitions. In 2017, a competition was held at the University of Oulu in Finland on its own new data set with quite interesting protocols, focused specifically on use in the field of mobile applications.
- Protocol 1: There is a difference in lighting and background. The datasets are recorded in different locations and differ in background and lighting.
The datasets are recorded in different locations and differ in background and lighting.
- Protocol 2: Various models of printers and screens were used for the attacks. Thus, the test set uses a technique that is not found in the training set
-Protocol 3: Sensor interchangeability. Videos of the real user and attacks are recorded on five different smartphones and used in the training dataset. To test the algorithm, video from another smartphone is used, which is not included in the training set.
- Protocol 4: includes all of the above factors.
The results were quite unexpected. As in any competition, there was no time to come up with brilliant ideas, so almost all participants took familiar architectures and refined them by fine-tuning, working with features and trying to somehow use other data sets for training. The prize solution showed an error on the fourth, most difficult protocol, about 10%. A brief description of the algorithms of the winners in the table just below:
-
GRADIENT
- Features are merged by color (using HSV and YCbCr color spaces), texture, and motion.

- Dynamic information is extracted from the given video sequence and time change maps in a single frame.
- This sequence is separately applied to all channels in the HSV and YCbCr color spaces, giving together a pair of three-channel images. For each image, the ROI (region-of-interest) is cropped based on the position of the eyes in the frame sequence and scaled to 160x160 pixels..
- Each ROI is divided into 3x3 and 5x5 rectangular areas, over which uniform LBP histograms of features are extracted, which are combined into two feature vectors with a dimension of 6018.
- Recursive Feature Elimination reduces dimension from 6018 to 1000.
- For each feature vector, classification based on SVM is performed and then averaged.|
- Features are merged by color (using HSV and YCbCr color spaces), texture, and motion.
-
SZCVI
- A frame sample is taken from each video, every sixth frame is taken
- Frame scaling up to 216×384
- Five VGG-like layers
- Results of individual frames within a sample are averaged
-
Recod
- SqueezeNet is trained on Imagenet
- Transfer learning on two datasets: CASIA and UVAD
- First the face is detected and scaled to 224×224 pixels.
 From each video of the training dataset, approximately every seventh frame is extracted, which is sent to ten CNNs.
From each video of the training dataset, approximately every seventh frame is extracted, which is sent to ten CNNs. - To obtain the final result, the values of individual frames are averaged.
- To improve efficiency, the obtained indicators are summarized in the generalized result of the basic method
-
CPqD
- Inception-v3 network trained on ImageNet
- Sigmoid activation function
- Based on the position of the eyes, the areas of the image containing the face are cropped and then scaled to 224x224 RGB |
It is clear that there are not many new ideas. All the same LBP, pre-trained meshes, texture and color analysis, pairwise frame analysis, etc. GRADIANT looks like the most well-designed from a system point of view, it mixes various features, works in different color spaces, and features are being cleaned. He won the competition.
The competition showed the existing limitations very clearly. First of all, this is the limitation and lack of balance of existing datasets for training. First, they represent a fairly limited number of people (ranging from 15 people in NUAA to 1140 in MSU-USSA) and sessions, ambient light differences, facial expressions, recording devices used, camera angles, and types of attacks. At the same time, in real conditions, the camera model, sensor quality, shooting conditions, focal length and shutter speed, background and environment often turn out to be decisive for image analysis. Secondly, the analysis methods themselves are much more focused on the analysis of individual sections of the image without significant processing of the scene environment itself. For example, in the CASIA set, many examples of attacks are presented in the form of an image of a person who holds a photograph in front of his face. Obviously, the characteristic position of the hands, the borders of the sheet with the photo are visible, the hair, neck and head, and so on can be seen .
First of all, this is the limitation and lack of balance of existing datasets for training. First, they represent a fairly limited number of people (ranging from 15 people in NUAA to 1140 in MSU-USSA) and sessions, ambient light differences, facial expressions, recording devices used, camera angles, and types of attacks. At the same time, in real conditions, the camera model, sensor quality, shooting conditions, focal length and shutter speed, background and environment often turn out to be decisive for image analysis. Secondly, the analysis methods themselves are much more focused on the analysis of individual sections of the image without significant processing of the scene environment itself. For example, in the CASIA set, many examples of attacks are presented in the form of an image of a person who holds a photograph in front of his face. Obviously, the characteristic position of the hands, the borders of the sheet with the photo are visible, the hair, neck and head, and so on can be seen . .. But solutions using the analysis of the entire scene and the position of the person were not presented, all algorithms worked only with a section selected from the entire scene faces.
.. But solutions using the analysis of the entire scene and the position of the person were not presented, all algorithms worked only with a section selected from the entire scene faces.
Another promising competition has recently been proposed on a new 30 GB data set of our own design. According to the terms of the competition, the detection of a mask worn on the face, the fact of taking a printed photograph and presenting a video recording on the screen instead of a real face must be performed. It is likely that, based on its results, we will see a conceptually new solution.
Of course, there are solutions based on “non-standard approaches”. Let's move on to them with the hope of improving the current state of affairs. For example, it was proposed to use the method of remote photoplethysmography (rPPG - remote photoplethysmography), which makes it possible to detect the beating of a person's pulse from a video image. The idea is that when light hits a living person's face, some of the light will be reflected, some will be scattered, and some will be absorbed by the skin and tissues of the face. In this case, the picture will be different depending on the degree of tissue filling with blood. Thus, it is possible to track the pulsation of blood in the vessels of the face and, accordingly, to detect the pulse. Of course, if you cover your face with a mask or present the screen of your phone, you will not be able to detect any pulsation. Based on this principle, Liu et al. proposed splitting the face image into sections, detecting the pulse using remote photoplethysmography, comparing different areas in pairs for counting the pulse, and building maps to detect the presence or absence of a mask, as well as comparing pulses in different parts of the face.
In this case, the picture will be different depending on the degree of tissue filling with blood. Thus, it is possible to track the pulsation of blood in the vessels of the face and, accordingly, to detect the pulse. Of course, if you cover your face with a mask or present the screen of your phone, you will not be able to detect any pulsation. Based on this principle, Liu et al. proposed splitting the face image into sections, detecting the pulse using remote photoplethysmography, comparing different areas in pairs for counting the pulse, and building maps to detect the presence or absence of a mask, as well as comparing pulses in different parts of the face.
The work showed an HTER value of about 10%, confirming the fundamental applicability of the method. There are several more works confirming the promise of this approach
(CVPR 2018) J. H.-Ortega et al. Time Analysis of Pulsebased Face Anti-Spoofing in Visible and NIR
(2016) X. Li. et al. Generalized face anti-spoofing by detecting pulse from face videos
(2016) J. Chen et al. Realsense = real heart rate: Illumination invariant heart rate estimation from videos
Chen et al. Realsense = real heart rate: Illumination invariant heart rate estimation from videos
(2014) H. E. Tasli et al. Remote PPG based vital sign measurement using adaptive facial regions
photoplethysmography. For each of the real face images, a 3D model was reconstructed using a neural network and named with a depth map. The fake images were given a depth map consisting of zeros, after all, it's just a piece of paper or a device screen! These characteristics were taken as "true", the neural networks were trained on their own SiW dataset. Then, a 3D face mask was superimposed on the input image, a depth map and pulse were calculated for it, and all this was tied together in a rather complex pipeline. As a result, the method showed an accuracy of about 10 percent on the competitive OULU dataset. Interestingly, the winner of the competition, organized by the University of Oulu, built an algorithm on binary classification patterns, blink tracking and other "hand-crafted" features, and his solution also had an accuracy of about 10%. The winnings amounted to only about half a percent! In favor of the new combined technology is the fact that the algorithm was trained on its own dataset, and tested on OULU, improving the result of the winner. Which indicates some portability of the results from dataset to dataset, and what the hell is not joking, perhaps in real life. However, when trying to perform training on other datasets - CASIA and ReplayAttack, the result was again about 28%. Of course, this outperforms other algorithms when training on various data sets, but with such accuracy values, there can be no question of any industrial use!
The winnings amounted to only about half a percent! In favor of the new combined technology is the fact that the algorithm was trained on its own dataset, and tested on OULU, improving the result of the winner. Which indicates some portability of the results from dataset to dataset, and what the hell is not joking, perhaps in real life. However, when trying to perform training on other datasets - CASIA and ReplayAttack, the result was again about 28%. Of course, this outperforms other algorithms when training on various data sets, but with such accuracy values, there can be no question of any industrial use!
Another approach was proposed by Wang and colleagues in a recent 2019 paper. It was noted that in the analysis of micromovements of the face, turns and displacements of the head are noticeable, leading to a characteristic change in the angles and relative distances between the features on the face. So when the face is shifted to the sides horizontally, the angle between the nose and the ear increases. But, if you move a sheet of paper with a picture in the same way, the angle will decrease! For illustration, it is worth quoting a drawing from the work.
But, if you move a sheet of paper with a picture in the same way, the angle will decrease! For illustration, it is worth quoting a drawing from the work.
Based on this principle, the authors built a whole learning block to transfer data between layers of the neural network. It took into account the "wrong offsets" for each frame in a sequence of two frames, and this allowed the results to be used in the next block of analysis of long-term dependencies based on the GRU Gated Recurrent Unit. Then all the features were concatenated, the loss function was calculated, and the final classification was performed. This allowed for a slightly better result on the OULU dataset, but the problem of dependence on the training data remained, since for the CASIA-MFSD and Replay-Attack pair, the figures were 17.5 and 24 percent, respectively.
In the end, it is worth noting the work of Tencent specialists, who proposed to change the very method of obtaining the original video image. Instead of passively observing the scene, they proposed to dynamically illuminate the face and read reflections. The principle of active irradiation of an object has long been used in various types of location systems, therefore, its use for studying a face looks very logical. Obviously, there are not enough features in the image itself for reliable identification, and illuminating the screen of a phone or tablet with a sequence of light symbols (light CAPTCHA in the authors' terminology) can help a lot. Next, the difference in scattering and reflection over a pair of frames is determined, and the results are fed to a multitasking neural network for further processing on a depth map and calculating various loss functions. Finally, the normalized illuminance frames are regressed. The authors did not analyze the generalizing ability of their algorithm on other data sets and trained it on their own closed dataset. The result is about 1% and it is reported that the model has already been deployed for real use.
Instead of passively observing the scene, they proposed to dynamically illuminate the face and read reflections. The principle of active irradiation of an object has long been used in various types of location systems, therefore, its use for studying a face looks very logical. Obviously, there are not enough features in the image itself for reliable identification, and illuminating the screen of a phone or tablet with a sequence of light symbols (light CAPTCHA in the authors' terminology) can help a lot. Next, the difference in scattering and reflection over a pair of frames is determined, and the results are fed to a multitasking neural network for further processing on a depth map and calculating various loss functions. Finally, the normalized illuminance frames are regressed. The authors did not analyze the generalizing ability of their algorithm on other data sets and trained it on their own closed dataset. The result is about 1% and it is reported that the model has already been deployed for real use.
Until 2017, the face anti-spoofing area was not very active. But 2019 has already presented a whole series of works, which is associated with the aggressive promotion of mobile face identification technologies, primarily by Apple. In addition, banks have become interested in facial recognition technologies. Many new people have entered the industry, which allows us to hope for rapid progress. But so far, despite the beautiful titles of publications, the generalizing ability of the algorithms remains very weak and does not allow us to talk about any suitability for practical use.
Conclusion. And finally, I will say that…
- Local binary patterns, tracking of blinking, breathing, movements and other manually constructed features have not lost their significance at all. This is primarily due to the fact that deep learning in the field of face anti-spoofing is still quite naive.
- It is quite obvious that in the "same" solution, several methods will be merged.
 Reflection analysis, scattering, depth maps should be used together. Most likely, adding an additional data channel will help, for example, voice recording and some kind of systemic approaches that will allow you to collect several technologies into a single system
Reflection analysis, scattering, depth maps should be used together. Most likely, adding an additional data channel will help, for example, voice recording and some kind of systemic approaches that will allow you to collect several technologies into a single system - Almost all face recognition technologies are used in face anti-spoofing (cap!) Everything that was developed for face recognition, in one form or another, has also been used for attack analysis
- Existing datasets have reached saturation. Of the ten core datasets, five were able to achieve zero error. This already speaks, for example, about the efficiency of methods based on depth maps, but does not improve the generalization ability. We need new data and new experiments on them
- There is a clear imbalance between the degree of development of face recognition and face anti-spoofing. Recognition technologies are significantly ahead of security systems. Moreover, it is the lack of reliable protection systems that hinders the practical application of face recognition systems.