Match com sign in page
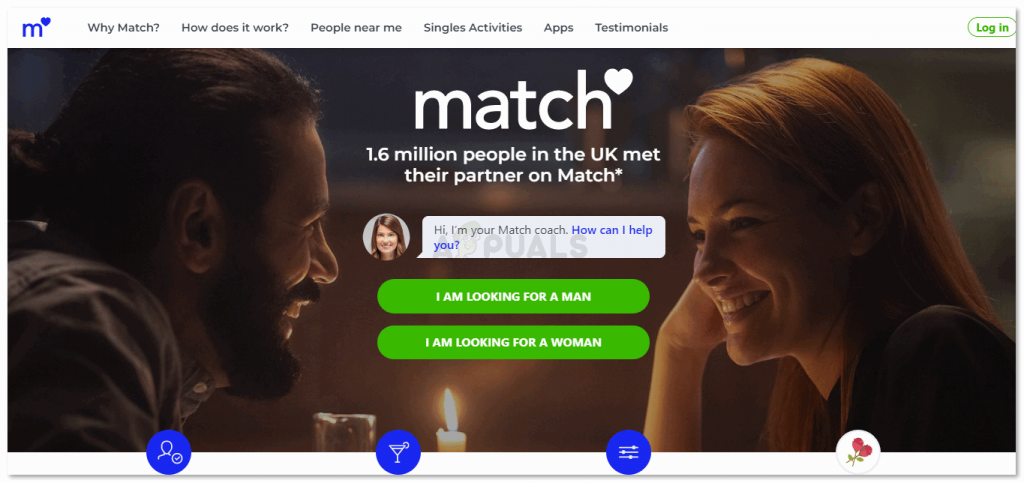
Online Dating Site - Register For Free on Match UK!
Start Something Real
356,000 conversations start every month on Match****
2.6M people have already met someone on Match*. Could you be next?
1 in 5 Brits knows a Match couple*****
Why Match?
Find a person you match with
Our members are looking for their very own love story and we do everything to help them achieve it.
Check out our detailed profiles
On Match, dating profiles are very detailed. You can find matches using the criteria search or just browse through the array of members’ profiles.
Lara
Dating coach
Need a helping hand?
You can count on Lara, your virtual coach, for everything you need: dating advice, personalised selections, tips to improve your profile, and icebreakers for your first messages.
Bye bye routine, hello surprise.
Come and meet singles near you at one of our vibrant and informal Match nights.
Try a real video date
See your date’s reactions for the very first time, from the safety and comfort of a Match video call!
2.
Broad visibility of your profile
There’s more to Match than just Match. Register with us, create your perfect online dating profile and so you don’t miss out on a chance to find that special someone, your profile can be made visible to members of our dating service for the over 50s if you choose it. That means you will be able to see more profiles and increase your chances of being contacted!
For more information about your profile visibility click here.
Trust and safety
We want Match to be a fun, safe online dating site where you can meet serious, committed singles ready for a real relationship. The safety of our clients is our top priority, and we work hard to keep our site safe. We moderate every single profile picture and description on our site, and the protection of your personal data is our priority.
Plus if you ever feel uncomfortable about a profile or a message you receive you can always block or report a member to our moderators. They’ll be happy to help. We also have lots of tips about making sure you stay safe while you’re using our site and when you decide it’s time to meet in real life. Just take a look in our help centre.
They’ll be happy to help. We also have lots of tips about making sure you stay safe while you’re using our site and when you decide it’s time to meet in real life. Just take a look in our help centre.
Cyber-bullying leads nowhere. Least of all to love.
Match is fighting cyber-bullying to give you a safer dating experience.
If you receive messages which make you feel uncomfortable, you can:
- - Report a profile to alert the Moderation and Safety team.
- - Block a profile to avoid being contacted by that person again.
Our virtual coach Lara helps prevent and detect cyberbullying. She will intervene in the event of too many unanswered messages being sent to the same person. Lara will help you put an end to this situation.
Learn more
Want to be more in control?
With Match, you’re in charge. You can visit singles’ profiles without alerting them, or set your preferences so you can only be contacted by singles who match your search criteria. The choice is yours!
The choice is yours!
Choose “Incognito Mode”
Incognito mode is your online dating superpower. It lets you view other people’s profiles discreetly – they won’t know you’ve visited – and ensures you only appear to people you know you’re interested in. Which means less hassle – and more chance of finding a date!
Opt for “Zen Mode”
Zen mode is great when you need a little peace and quiet. Activate it and only people who match your criteria will be able to contact you – so you know they’re worth a look.
How to encounter dating?
You are three steps away from dating your special someone
Tell us who you are!
Talk about yourself. The secret? Be natural, honest and spontaneous. A few lines are enough to make an impression.
Why not add a bit of humour, too?
Be precise: the more search criteria you complete, the greater your chances are of being contacted by singles who share the same interests as you.
Share your photos. Create an album that reflects your personality.
Find the right person
Meet the person who’s right for you thanks to our detailed search.
Discover our personalised selection of detailed dating profiles.
Come and meet other singles at our Match evenings and activities.
Discuss
Don’t know how to kick start the conversation?
Tell them about the little details that attracted you to their online dating profile or discuss your shared interests.
Or be creative and share a music link, or a GIF!
Read our advice articles to make your profile as attractive as possible and find tips on how to break the ice.
Discover our dating advice
Our singles nights and activities
Laid-back, original and fun, Match events have already attracted over 300,000 members. Join the community!
Make space in your diary! Come to our singles nights and events for your age group in your area.
Meet singles through a shared interest at one of our many activities or over a drink at one of our free drinks events.
Don’t want to come on your own? Ask your friends to come too!
What are you waiting for?
Book your place at an upcoming singles event in the UK.
- Discover our singles nights in London.
Eric,
Sarha
Kate,
Simon
Laura,
Jon
Lucy,
Emma
Our success stories
2.6M people have already met someone on Match*. Could you be next?
Here are just a few of them: real-life single men and women who were ready to start a relationship and trusted Match to help them find it. Maybe the next success story we can tell will be yours!
Read their stories
Match dating app
Download the Match online dating app and you’re always ready to check out profiles near you, and chat with real, committed singles ready for a real relationship. Free for iOS and Android, it puts all the power of Match in the palm of your hand for a faster, smoother online dating experience.
Download on the App StoreGet it on Google Play
How do you show you’re ready for a real story?
Be calm. Be kind. Be yourself.
Online dating may have led to an increase in casual dating and hook-up culture.
But people looking to meet singles on Match have chosen our service because they’re ready to start a real story. So how do you make sure someone you meet online understands you’re serious, and how do you establish those expectations?
The secret isn’t really a secret, and it’s something you’ve almost certainly been told before. The key is to be yourself, be kind and be calm. And it all starts with writing your profile.
Discover mature dating on Match and browse senior singles on our website.
Think about the sort of person you would like to share a long-term relationship with.
Looks matter, for sure. But the chances are you would choose someone who is genuine, considerate, interested in you and who makes you laugh. There’s nothing wrong with that: it’s the most human thing of all: we want to be with people who make us happy.
When you write your online dating profile, make sure you’re the sort of person you would want to be with. Try to resist the temptation to talk just about yourself: make it clear you’re interested in other people too. What would you like to do together with your date? What do you enjoy in people? Show that you are someone who is great company, not just someone who expects people want to be with them.
When you’re talking to your date, either online or, eventually, in real life, don’t be afraid to listen more than you talk.
Be interested in what your date is telling you about themselves. Ask questions, smile and laugh. Focus on the interests and experiences you share, and don’t get hung up on the negatives. Because if you seem like someone who people want to be with, they’ll want to be with you.
Meet singles near you
In Manchester, Edinburgh, London, Portsmouth…
Wherever you are, there are people waiting to meet you! Still not convinced?
Register and see for yourself!
London dating
Dates in London: Are you single and living in London? Register free for Match and browse thousands of profiles of other single Londoners. Arrange dates in the capital at our singles events.
Arrange dates in the capital at our singles events.
London Dating
Edinburgh dating
Dates in Edinburgh: Want to meet eligible Edinburgh singles? Browse our wide selection of profiles or attend a singles event in the Scottish capital.
Edinburgh Dating
Manchester dating
Dates in Manchester: Want great dates in Manchester? Register on Match and meet singles in Manchester on our website, or at a drinks event or a meet-up activity organised by Match.
Manchester Dating
With thousands of singles up and down the UK ready to start a real relationship, why not check out who’s looking for someone like you in a city near you.
Liverpool datingLeicester datingBristol datingGlasgow datingBelfast datingBirmingham datingCambridge datingAberdeen datingCardiff datingLeeds datingJersey datingNewcastle datingNottingham datingSheffield dating
Ready to widen your search?
Check out singles in your region and get chatting!
Devon datingLincolnshire datingEssex datingHampshire datingHertfordshire datingKent datingYorkshire datingSurrey datingBerkshire datingLancashire datingSussex datingChannel Islands datingMidlands datingEast England datingNorforlk datingNorth England datingSouth England dating
Meet singles in UK from your area
Language matters when you’re online dating!
Words of love and everyday life
Don’t be afraid of words! All the new casual dating sites that have appeared recently have transformed the game of seduction into something like a video game.
The result? Many singles have given up dating altogether as it is just too exhausting! However, many singles are looking for serious, deeper and more authentic encounters and a long-term relationship.
The key to this new demand for authenticity is through words. Yes, even in the instant world of online dating, words are what really count.
Let’s start with the words you use to describe yourself. They say a picture is worth a thousand words, but our singles consistently tell us that a profile description matters more to them than a photo***.
It’s important, especially on a serious dating site, that you take the time to make your written presentation as good as it can be, and reveal your true self honestly and carefully.
And words can break the ice! It can be hard to introduce yourself to a single you find interesting; it is always difficult to find the right way to approach them and find THE message that will attract their attention. Anyone can write ‘hello’, but is it going to make you stand out from the crowd during your encounters? In dating first impressions count, and the first words you exchange online can make all the difference.
Finally, words say a lot during a first date in real life.
Looks really aren’t everything, and when you’re finally face-to-face in front of a person, you can’t hide behind your screen any more! But rest assured, people generally prefer good humour to good looks on a first date, and they want someone with whom they can share an interesting conversation. The most important thing is to be yourself and stay as natural as possible.
Recommended by our customers
A dating brand you can trust
Every day, thounds of committed singles trust Match. Their feedback is close to our hearts. Why? Because listening to real customers helps us create real relationships. With 2.6 million people having already met someone on Match, could you be next?
Trustpilot
Start meeting singles who are ready to commit today
Our services
- Singles nights & events
- Dating & relationship advice
- Help/Contact us
- Success stories
- Advertising
- Press
- Affiliation
- Business development
- Affiny.
 co.uk
co.uk - Match TV Advert
Visit our pages
© 2022 Match | Match is a meetic network website.
Broad visibility of your profile: By creating your profile on Match, it will be visible on the local variants of our service which use the same platform operated under different brand names. For more information about the terms of your profile’s extended visibility, click here.
For any complaints and enquiries you may contact us here. If we are not able to resolve a complaint, you may submit it through the EU online dispute resolution platform at http://ec.europa.eu/odr. Please note that a complaint submitted through the online platform will not be considered unless you have raised it with us first.
*Data based on an extrapolation from Dynata survey conducted in July 2021, among a representative sample of 2 004 respondents aged 18+ in the UK which has been combined with the total population of this age group (Source Eurostat 2020). 6% of interviewees claim having already met someone on Match.
**All profile pictures and descriptions are moderated.
***Data based on an internal study conducted between October 29th and November 16th 2018, among a representative sample of 1552 respondents aged 18+ in the UK.
****Internal data - average number of conversations (=2 messages exchanged between 2 members) starting on Match every month - July to September 2021.
*****Survey conducted by Dynata in July 2021, among a representative sample of 2 004 persons aged 18+ in the UK. 21% claim they know a couple who have met on Match.
We are a member of the Online Dating Association (ODA). We are committed to maintaining standards, protecting users and giving those users assurance as outlined in Our Guiding Principles. Further information about ODA can be found here. A link to our customer service arrangements is provided here.
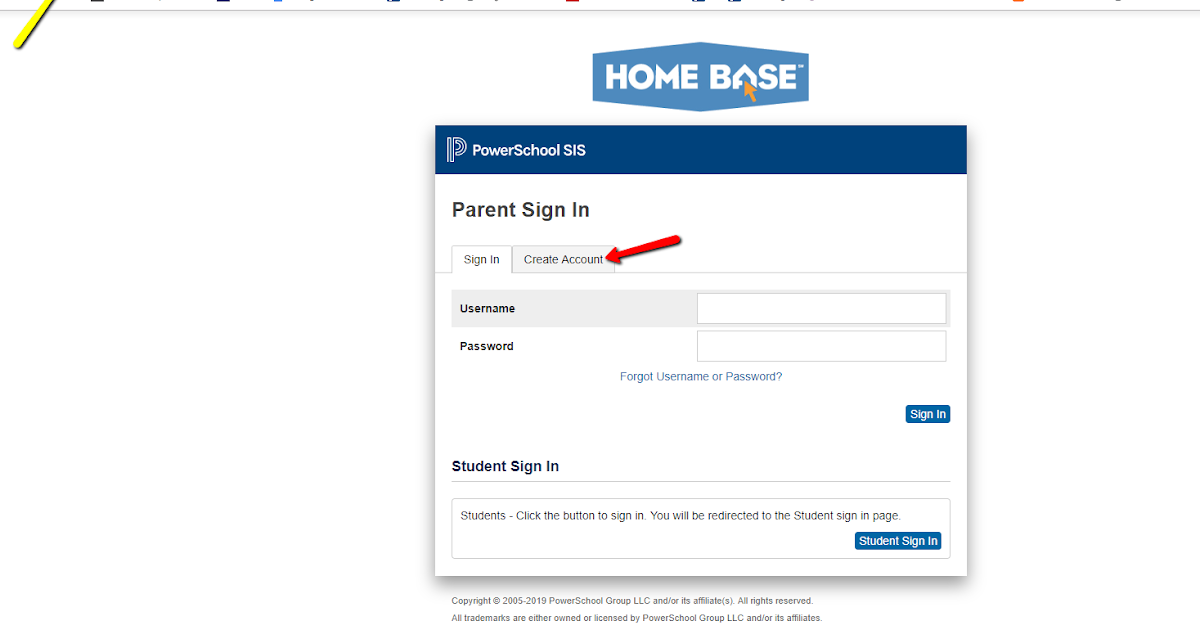
Match.com Login to My Account 2022
Match.com LoginContents
- 1 Match.com Login
- 2 Match.
 com Login Requirements
com Login Requirements - 3 How to Login to Your Match.com Account
- 4 How to Reset Match.com Password
- 5 Match.com Login Help and Contact Information
- 6 FAQs
- 7 Is match only working in the USA?
- 8 What to do if I face any issue in Match com login?
- 9 What should I take care of while logging in to Match Login?
- 9.1 Related Posts
Match.com Login: We are looking forward to seeing you in our next article. Today’s article will cover all details about Match com login.
This is the official website of Match.com login. It also contains all necessary information for login to Match.com. Match com is a fascinating website. This online dating site offers its services in 50 different countries. It can also be used in 12 languages. Dallas is the headquarters of match.com.
One of the largest match groups manages the company. It also offers other online dating services.
Many offices manage all back-office work. They are located in Dallas and Beijing, Rio De Janeiro, Tokyo, West Hollywood, and San Francisco. We now have an idea of the portal. Let us look at how to log in to match.com.
Visit its official portal. Match.com login Your account is where you can find your perfect mate or partner with whom to share your whole life.
We’ll be demonstrating the steps of Match.com login to your account but login is required for match.com accounts.
Match.com Login RequirementsLogin to Match com will require the following items.
- Official website of Match.com
- Your username and password
- Upgrading your web browser
- Laptop, tablet, smartphone, or laptop.
- You can have an uninterrupted internet connection and get fast data speeds.
We hope that you now have all of the above. Then we can start moving toward the next steps.
How to Login to Your Match. com Account
com AccountTo access match com login to an account, you will need to follow these steps.
- Visit the official site of www.match.com/messages.
- You will be on the Match Login page.
- Please fill in the empty spaces with your Email address and password.
- Next, click on the grey oval-shaped sign-in button to access match.com login to your account.
These are the steps you need to take to reset your match.com password.
- Visit the official site of www.match.com/messages.
- You will be on the Match Login page.
- Find that small font Forgot the password in blue font.
- Click on this to see the prompt asking for an email ID.
- Enter your email ID and click Send Email.
An email will be sent to you describing the next steps.
Match.com Login Help and Contact InformationDo you face any login problem or any kind of technical difficulty in the login match then please visit this site – https://match. custhelp.com/app/ask/src_domain/in.a.caom and fill in the required details, a asked and lastly click on send button, your query will be resolved very soon.
custhelp.com/app/ask/src_domain/in.a.caom and fill in the required details, a asked and lastly click on send button, your query will be resolved very soon.
You can use match USA login if you’re in the USA. If you’re travelling to the USA, make sure you verify the URL address.
What to do if I face any issue in Match com login?For more information, please refer to our match com login assistance and contact details.
What should I take care of while logging in to Match Login?Make sure to uncheck the blue box when you use a public computer.
This website uses cookies to improve your experience. We'll assume you're ok with this, but you can opt-out if you wish. Cookie settingsACCEPT
Mapping Requests to Clients in a Multi-Tenant Solution - Azure Architecture Center
Each time a request enters an application, you must determine the client that the request is for. If you have client-specific infrastructure, which may even be hosted in different geographies, you need to map the incoming request to the client. You then need to forward the request to the physical infrastructure that hosts this tenant's resources, as shown below.
If you have client-specific infrastructure, which may even be hosted in different geographies, you need to map the incoming request to the client. You then need to forward the request to the physical infrastructure that hosts this tenant's resources, as shown below.
On this page, we provide guidance to technical decision makers about approaches that can be considered to match requests with the appropriate client and trade-offs associated with approaches.
Note
This page mainly deals with HTTP-based applications such as websites and APIs. However, many of these same basic principles apply to multi-tenant applications using other communication protocols.
Client identification approaches
There are several ways to identify a client for an incoming request.
Domain names
If you are using domain or subdomain names for a particular client, chances are requests can be easily mapped to clients using the Host header or another HTTP header that includes the original host name for each request.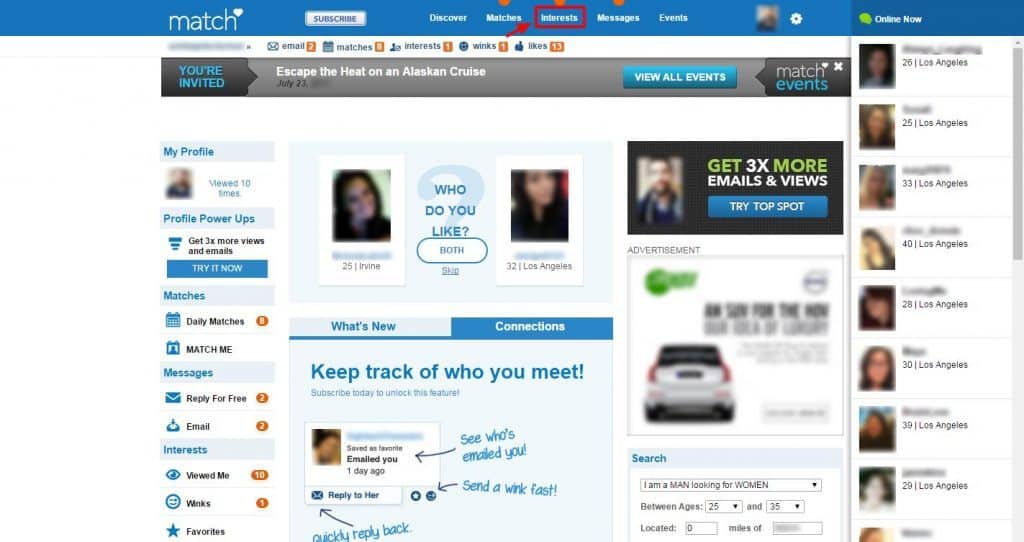
However, consider the following questions:
- How will users know which domain name to use to access the service?
- Do you have a central entry point, such as a landing page or login page, that all clients use? If you do, how will users determine which client they need access to?
- What other information is used to verify client access, such as authorization tokens? Do auth tokens include tenant-specific domain names?
HTTP Request Properties
If you are not using client-specific domain names, you may still be able to use HTTP request aspects to determine which client a particular request is for. For example, consider an HTTP request specifying a client name as tailwind traders . This can be reported as follows:
- URL path structure , for example
https://app.contoso.com/tailwindtraders/. - Query string in the URL, such as
https://contoso.. com/app?tenant=tailwindtraders
com/app?tenant=tailwindtraders - Custom HTTP request header , for example
X-Tenant-Id: tailwindtraders.
Important!
Custom HTTP request headers are not useful when HTTP GET requests are issued from a web browser or where requests are handled by some type of web proxy. Custom HTTP headers should only be used for GET operations when creating an API, or if you control the client that issues the request and the web proxy is not included in the request processing chain.
The following questions should be considered when using this approach:
- Will users know how to access the service? For example, if a query string is used to identify clients, will the central landing page need to direct users to the correct client by adding the query string?
- Do you have a central entry point, such as a landing page or login page, that all clients use? If you do, how will users determine which client they need access to?
- Does your application provide an API? For example, is the web application a single page application (SPA) or a mobile application with an API backend? Otherwise, you can use an API gateway or reverse proxy to match clients.
Token claims
Many applications use claims-based authentication and authorization protocols such as OAuth 2.0 or SAML. These protocols provide authorization tokens to the client. The marker contains a set of claims that are part of the client application or user details. Claims can be used to pass information such as the user's email address. The system can then include the user's email address, find a mapping between users and the client, and then forward the request to the appropriate deployment. Alternatively, you can even include client mapping in the identity system and add a client ID claim to the token.
When using claims to match requests with clients, consider the following questions:
- Will a claim be used to identify a client? Which statement will you use?
- Can a user be a member of multiple clients? If possible, how will users choose the clients they would like to work with?
- Is there a centralized authentication and authorization system for all clients? If not, how do you ensure that all token centers issue consistent tokens and claims?
API keys
Many applications provide an API. This can be for internal use within an organization or for external use by partners or customers. A common way to authenticate to an API is to use the API key . API keys are provided with each request and can be used to find a client.
This can be for internal use within an organization or for external use by partners or customers. A common way to authenticate to an API is to use the API key . API keys are provided with each request and can be used to find a client.
API keys can be generated in several ways. A common approach is to create a cryptographically random value and store it in a lookup table along with the client ID. When a request is received, the system looks up the API key in the lookup table and then matches it with the client ID. Another approach is to create a friendly string with the client ID included in it and then digitally sign the key using an approach such as HMAC. As each request is processed, the signature must be verified and then the client ID retrieved.
Note
API keys are not highly secure because they must be manually created and managed, and because they do not contain claims. A more modern and secure approach is to use a claims-based authorization mechanism with short tokens such as OAuth 2. 0 or OpenID Connect.
0 or OpenID Connect.
Answer the following questions.
- How do I generate and issue API keys?
- How will API clients securely obtain and store an API key?
- Do API keys need to expire after a certain period of time? How to change client API keys without downtime?
- Does simply using customer-deployed API keys provide an adequate level of security for the API?
Note
API keys do not match passwords. API keys must be generated by the system and must be unique across all clients so that each API key can be uniquely associated with a single client. API gateways such as Azure API Management can create and manage API keys, validate keys on incoming requests, and map keys to individual API subscribers.
Client certificates
Client certificate authentication, sometimes referred to as mutual tls (mTLS), is commonly used for communication between services. Client certificates provide a secure way to authenticate clients. Like tokens and claims, client certificates provide attributes that can be used to identify a client. For example, subject of the certificate may contain the user's email address, which can be used to locate the client.
Like tokens and claims, client certificates provide attributes that can be used to identify a client. For example, subject of the certificate may contain the user's email address, which can be used to locate the client.
Consider the following when planning to use client certificates for client mapping:
- How do you securely issue and renew client certificates that are trusted by your service? Client certificates can be tricky to work with because they require a special infrastructure to manage and issue certificates.
- Will client certificates be used only for initial login requests, or will they be attached to all requests to the service?
- Will the process of issuing and managing certificates become unmanageable if you have a large number of clients?
- How do I implement a mapping between a client certificate and a client?
Reverse proxies
A reverse proxy, also known as an application proxy, can be used to route HTTP requests. A reverse proxy server receives a request from an incoming traffic endpoint and can forward the request to one of many internal endpoints. Reverse proxies are useful for multi-tenant applications because they can perform a mapping between some part of the request details, offloading the task from the application infrastructure.
A reverse proxy server receives a request from an incoming traffic endpoint and can forward the request to one of many internal endpoints. Reverse proxies are useful for multi-tenant applications because they can perform a mapping between some part of the request details, offloading the task from the application infrastructure.
Many reverse proxies can use request properties to make decisions about client routing. They can check the final domain name, URL path, query string, HTTP headers, and even token claims.
Azure uses the following common reverse proxies:
- Azure Front Door is a global load balancer and web application firewall. It uses the Microsoft edge global network to build fast, secure, and highly scalable web applications.
- Azure Application Gateway is a managed web traffic load balancer that is deployed in the same physical region as the backend service.
- Azure API Management is optimized for API traffic.
- Commercial and open source technologies (that you self-host) include nginx, Traefik, and HAProxy.
Checking requests
It is important to make sure that your application checks that all received requests are allowed for the client. For example, if an application uses a custom domain name to match requests to a client, the application must still check that every request received by the application is allowed for that client. Even though the request contains a domain name or other client identifier, it does not mean that you should automatically grant access. When using OAuth 2.0, validation is done by validating claims room and area .
Note
This is part of the zero trust security design principle in the Microsoft Azure Well-Architected Framework. Consider the following when implementing request validation:
- How do I authorize all requests to an application? Requests must be authorized no matter what approach you use to map them to the physical infrastructure.
- Use trusted and widely used authentication and authorization frameworks and middleware instead of implementing all the validation logic yourself.
 For example, don't write token signature verification logic or a client certificate encryption library. Instead, use application platform features (or well-known trusted packages) that have been tried and tested.
For example, don't write token signature verification logic or a client certificate encryption library. Instead, use application platform features (or well-known trusted packages) that have been tried and tested.
Performance
The client mapping logic is most likely executed on every request to the application. Consider how well the client matching process will scale as the solution grows. For example, if you query a database table as part of a client mapping, will the database support a large amount of load? If client matching requires token decryption, will the computational requirements become too high over time? If your traffic is rather modest, then this is unlikely to affect the overall performance. However, if you have a scalable application, the cost associated with this mapping can become significant.
Session affinity
One approach to reduce the performance cost of the client mapping logic is to use session affinity . Instead of matching on every request, consider computing information only on the first request for each session. The application then provides client with session cookie . The client passes the session cookie back to the service with all subsequent client requests within that session.
The application then provides client with session cookie . The client passes the session cookie back to the service with all subsequent client requests within that session.
Note
Many network and application services in Azure can issue session cookies and routing requests in native code using session affinity.
Answer the following questions.
- Can session affinity be used to reduce the cost of matching requests to clients?
- What services are used to route requests to physical deployments on a per-tenant basis? Do these services support cookie-based session affinity?
Client Migration
Clients often need to be moved to a new infrastructure as part of the client lifecycle. When a client moves to a new deployment, the HTTP endpoints they access may change. In this case, you need to update the client matching process. You may need to consider the following:
- If your application uses domain names for mapping requests, you may also need to change the DNS during migration.
 The DNS change may take time to propagate to clients, depending on the lifetime of the DNS records in the DNS service.
The DNS change may take time to propagate to clients, depending on the lifetime of the DNS records in the DNS service. - If the migration changes the addresses of any endpoints during the migration, consider temporarily redirecting client requests to a maintenance page that updates automatically.
Contributors
This article is supported by Microsoft. It was originally written by the following contributors.
Subject author:
- Daniel Scott-Rainsford | Partner Technology Strategist
Other members:
- John Downings | Principal Customer Engineer, FastTrack for Azure
- Paolo Salvatori | Principal Customer Engineer, FastTrack for Azure
- Arsen Vladimirsky | Principal Customer Engineer, FastTrack for Azure
To view LinkedIn profiles that are not public, sign in to LinkedIn.
What to do next
Learn about best practices for dealing with domain names in a multi-tenant application.
Creating a Login - SQL Server
- Article
- Reading takes 10 minutes
Applies to: SQL Server (all supported versions) Azure SQL database SQL Managed Instance Azure Azure Synapse Analytics Analytics Platform System (PDW)
This article describes how to create a login in SQL Server Database or Azure SQL Database using SQL Server Management Studio (SSMS) or Transact-SQL. The login is the identity of the user or process connecting to the instance of SQL Server.
History
A login is a security principal that a security system can use to authenticate a person or entity. Users require a login to connect to SQL Server. You can create a login based on a Windows subject (for example, a Windows domain user or group), or you can create a login that is not based on a Windows subject (for example, a SQL Server login).
Note
To use SQL Server authentication, the database engine must use mixed mode authentication. For more information, see Selecting an Authentication Mode.
Azure SQL introduced Azure Active Directory Server Principals (logins) to be used for authentication against Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics (dedicated SQL pools only).
As security principals, permissions can be granted to logins. The login area is the entire database engine. To connect to a specific database on an instance of SQL Server, the login must be mapped to a database user. Permissions within a database are granted and denied to the database user, not the login. Permissions that are scoped to the entire instance of SQL Server (for example, permission CREATE ENDPOINT ) can be provided to the login.
Note
When a login connects to SQL Server, the identity is checked against the master database. Use contained database users to authenticate SQL Server and SQL Database connections at the database level. When using contained database users, a login is not required. A stand-alone database is a database that is isolated from other databases and from the instance of SQL Server or SQL Database (and the master database) that hosts the database. SQL Server supports contained database users for Windows and SQL Server authentication. When using SQL Database, combine contained database users with database-level firewall rules. For more information, see Contained Database Users - Create a Portable Database.
When using contained database users, a login is not required. A stand-alone database is a database that is isolated from other databases and from the instance of SQL Server or SQL Database (and the master database) that hosts the database. SQL Server supports contained database users for Windows and SQL Server authentication. When using SQL Database, combine contained database users with database-level firewall rules. For more information, see Contained Database Users - Create a Portable Database.
Security
SQL Server requires permission ALTER ANY LOGIN or ALTER LOGIN on the server.
SQL Database requires membership in role loginmanager .
Create a login using SSMS for SQL Server
-
In Object Explorer, expand the folder of the server instance where you want to create the login.
-
Right-click the folder Security and select Create and then Login.
 .. .
.. . -
In the Login - Create dialog box, on page General , enter the username in the Login field. In addition, select "Search", to open the dialog box "Select user" or "Group ".
If you select "Search... ":
-
In section "Selecting this object type 9 Select Object Types to open the Object Types dialog and select any or all of the following: Built-in security principals , Groups and Users . Built-in security principals and Users are selected by default When done select OK .
-
Under "From this location " select "Locations" to open the Locations dialog box and select one of the available server locations.
 When done, select OK .
When done, select OK . -
In the dialog box Enter the object names to select (examples) enter the user or group name you want to find. For more information, see Select Users, Computers, or Groups Dialog Box.
-
Select Advanced, for more search options. For more information, see Select Users, Computers, or Groups Dialog Box - Advanced Page.
-
Click OK .
-
-
To create a Windows principal-based login, select the Windows Authentication option. This option is selected by default.
-
To create a login stored in a SQL Server database, select SQL Server Authentication .
-
In the Password field, enter the password for the new user. Re-enter the password in field Password confirmation .
-
If you are changing an existing password, select Enter old password and enter the old password in the Old password field.
-
To ensure that passwords are used in accordance with password policies, select the option Require password policy . For more information, see Password Policy. This is the default value when you select option SQL Server 9 Authentication0041 .
-
To ensure that passwords are used in accordance with password expiration policies, select the option Set password expiration to . The option Require password policy must be selected for this check box to be available. This is the default value when you select the SQL Server Authentication option.
-
To allow the user to create a new password at the first login, select option User must change password at next login . For this checkbox to be available, the option Enforce password expiration must be selected. This is the default value when you select the SQL Server Authentication option.
-
-
To associate a login with an isolated security certificate, select Mapped to certificate, and then select the name of an existing certificate from the list.
-
To map a login to an isolated asymmetric key, select Mapped to asymmetric key, and then select an existing key name from the list.
-
To associate a login with a security credential, select the Mapped Credentials check box, and then select an existing credential from the list, or click the Add button to create a new credential. To remove the security credential mapping from a login, select credentials from mapped credential and click "Remove " button. For more information about credentials in general, see Credentials (Database Engine).
-
In the Default database list, select the default database for the desired login.
 By default, this parameter is set to Master .
By default, this parameter is set to Master . -
In the Default Language list, select the default language for login.
-
Click OK .
Advanced Options
The Login - Create dialog box also offers options on four additional pages: Server Roles , User Maps , Securable Objects and State .
Server roles
Note
These server roles are not available for SQL Database.
On page Server Roles lists all the possible roles that can be assigned with the new login. The following options are available:
Checkbox bulkadmin
Members of the bulkadmin fixed server role can execute a BULK INSERT statement.
Checkbox dbcreator
Members of the dbcreator fixed server role can create, modify, drop, and restore any database.
Check box diskadmin
Fixed server role elements diskadmin can manage disk files.
Checkbox processadmin
Members of the processadmin fixed server roles can terminate processes running in the Database Engine instance.
Checkbox Public
All SQL Server users, groups, and roles belong by default to the fixed server role public .
Check box securityadmin
Fixed server role members securityadmin manage logins and their properties. They can grant, deny, and revoke server-level permissions (GRANT, DENY, and REVOKE statements). They can also grant, deny, and revoke permissions at the database level (GRANT, DENY, and REVOKE statements). They can also reset passwords for SQL Server logins.
Checkbox serveradmin
Members of the serveradmin fixed server role can change server-level configuration settings and can also shut down the server.
Checkbox setupadmin
Members of the fixed server role setupadmin can add and remove linked servers and execute some system stored procedures.
Checkbox sysadmin
Members of fixed server roles sysadmin can perform any action in the database engine.
User Mapping
Page User Mapping lists all possible databases and database roles that can be applied at login time. The databases you select will determine the role memberships that are available for that login. The following options are available on this page.
Users associated with this login
Select the databases that this login can connect to. When you select a database, the roles allowed for it are displayed in the area Database role membership for: database_name .
Schema
Allows the login to access the following databases.
Database
List of databases available on this server.
User
Specify the database user to map to this login. By default, the database user has the same name as the login.
Default schema
Specifies the default schema for this user. When a user is created, its default schema is dbo . You can specify a default schema that does not already exist. You cannot specify a default schema for a user associated with a Windows group, certificate, or asymmetric key.
Guest account enabled for: database_name
Read-only attribute indicating that the Guest account is enabled on the selected database. Page Status of dialog box Login Properties for the Guest account allows you to enable or disable this account.
Database role membership for: database_name
Select roles for this user in the specified database. All users are members of public role in each database and cannot be deleted. For more information about database roles, see Database-Level Roles.
All users are members of public role in each database and cannot be deleted. For more information about database roles, see Database-Level Roles.
Securables
Page Securables lists all possible securables and the permissions on those objects that can be granted to a login. The following options are available on this page.
Top Grid
Contains one or more elements for which permissions can be set. The columns displayed in the upper grid change depending on the participant or protected object.
Adding elements to the upper grid:
-
Select Search (Search).
-
In the Add Objects dialog box, select one of the following options: certain objects... , all objects of types... or server server_name . Click OK .
Note
When server server_name is selected, the upper grid is automatically populated with all securable objects of these servers.
-
If you select Specific objects...
-
In the Select Objects dialog, under Select these object types, select Object Types... .
-
In the Select Object Types dialog box, select any or all of the following object types: Endpoints , Logins , Servers , Availability Groups and Server Roles . Click OK .
-
In section "Enter object names to select (examples) " click the button "Browse... ".
-
In the Object Search dialog box, select any of the available objects of the type selected in the Object Type Selection dialog box, and then click the OK button.
-
In the dialog box Select Objects , click button "OK ".
-
-
If you select All Object Types… , in the Select Object Types dialog box, select any or all of the following object types: . Click OK .
name ;
The name of each member or securable added to the mesh.
Type
Describes the type of each element.
Explicit tab
Contains the possible permissions for the securable object selected in the top grid. Not all of these options are available for all explicit permissions.
Permissions
Permission name.
Grantor
Authorizer.
Granted
Select to grant the login this permission. Clear the checkbox to revoke this permission.
Grant right
Reflects the state of the WITH GRANT option for the permission listed. The field is read-only. To apply this permission, use the GRANT statement.
To apply this permission, use the GRANT statement.
Deny
Select to deny the login in this permission. Clear the checkbox to revoke this permission.
Status
Status page of status lists some of the authentication and authorization options that you can configure for a selected SQL Server login.
The following options are available on this page.
Database Engine Connection Permission
When using this option, the selected login must be presented as a principal that can or may not be granted permission on the securable object.
Select Grant to grant the login CONNECT SQL permission. Select Deny to deny the login SQL CONNECT permission.
Login
When using this parameter, the selected login must be represented as an entry in a table. It will be assigned the values given here.
A disabled login continues to exist as an entry. But if he tries to connect to SQL Server, the login will not be authenticated.
But if he tries to connect to SQL Server, the login will not be authenticated.
Select this option to enable or disable the login. This option uses the ALTER LOGIN statement with the ENABLE or DISABLE option.
SQL Server Authentication
The Login Blocked check box is available only if the selected login connects using SQL Server Authentication and the login is blocked. This setting is read-only. To unlock a locked login, issue the ALTER LOGIN statement with the UNLOCK option.
How to create a login using Windows Authentication using T-SQL0041 Connect to an instance of the Database Engine.
On the standard panel, select Create request .
Copy the example below into a query box and click the Run button.
-- Create a login for SQL Server by specifying a server name and a Windows domain account name. CREATE LOGIN [\ ] FROM WINDOWS; GO
Creating a login with SQL Server Authentication using T-SQL
-
In Object Explorer, connect to an instance of the Database Engine.
-
On the standard panel, select Create request .
-
Copy the example below into a query box and click the Run button.
-- Creates the user "shcooper" for SQL Server using the security credential "RestrictedFaculty" -- The user login starts with the password "Baz1nga," but that password must be changed after the first login. CREATE LOGIN shcooper WITH PASSWORD = 'Baz1nga' MUST_CHANGE, CREDENTIAL = RestrictedFaculty; GO
For more information, see CREATE LOGIN (Transact-SQL).
Further actions. Steps to take after the login is created
After the login is created, the login can connect to SQL Server, but does not necessarily have sufficient permission to do any useful work. The following list provides links to basic login actions.
-
For more information about attaching a login to a role, see Attach to a Role.
-
For more information about authorizing a login to use a database, see Create a Database User.